Network Tools for penetration test
Nmap
Nmap used for the security scanner. This utility used by millions of people for network discovery, administration, and security auditing. From explaining port scanning basics for novices to detailing low-level packet crafting methods used by advanced hackers. Nmap can find open ports on the network.
Example port scan –
#nmap -sT 192.168.1.93/24 ( scan port 3-way handshake )
#nmap -sS 192.168.1.93/24 ( flag spoof)
#nmap -0 192.168.1.93/24 ( one host scan)
#nmap -sX 192.168.1.93/24 ( christmas scan )
#nmap -sF 192.168.1.93/24 ( fence scan )
#nmap -sN 192.168.1.93/24 ( null scan)
#nmap -PE 192.168.1.93/24 ( ping scan – layer 3 scan )
#nmap -sU 192.168.1.93/24 ( udp scan – layer 4 scan )
Christmas scan,fence scan and null scan – never get reply from windows based systems, only linux and unix system will work.
Kali Linux
Best Linux operating system for network security evaluation. Installation possible for both Windows and standalone systems.
Windows 10 based system can download from Microsoft store. Before installation, we have to enable windows subsystems settings.
Open control panel- Programs and Features-Turn Windows Features on or off- Enable windows subsystems for Linux- Ok
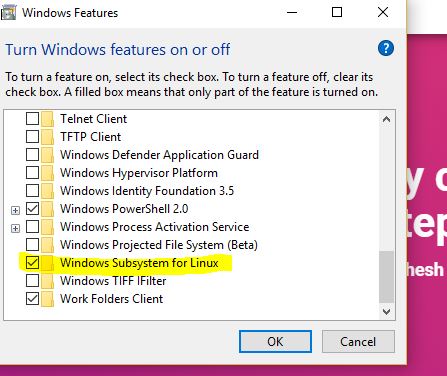
Once rebooted, open the Windows App store and search for the “Kali Linux” application, or alternatively click here to go there directly. Install the app and enjoy Kali!
Dnsenum
Dnsenum is a tool for DNS enumeration, which is the process of locating all DNS servers and DNS entries for an organization.
install this tool on kali
#apt-get install dnsenum
#dnsenum sukheshcs.com
The result will get full information about DNS and MX records details.
Wireshark
Wireshark tool for network packet analyzer and monitor network and capture packets.
Wireshark is a free and open source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education.
Install this tool on kali
#sudo apt-get install Wireshark
Wireshark is a free application that allows you to capture and view the data traveling back and forth on your network, providing the ability to drill down and read the contents of each packet – filtered to meet your specific needs.
Hping3
hping is a command-line oriented TCP/IP packet assembler/analyzer. The interface is inspired to the ping,unix command, but hping isn’t only able to send ICMP echo requests. It supports TCP, UDP, ICMP and RAW-IP protocols, has a traceroute mode, the ability to send files between a covered channel, and many other features.
While hping was mainly used as a security tool in the past, it can be used in many ways by people that don’t care about security to test networks and hosts. A subset of the stuff you can do using hping:
Firewall testing
Advanced port scanning
Network testing, using different protocols, TOS, fragmentation
Manual path MTU discovery
Advanced traceroute, under all the supported protocols
Remote OS fingerprinting
Remote uptime guessing
TCP/IP stacks auditing
hping can also be useful to students that are learning TCP/IP.
install this tool on kali
#sudo apt-get install hping3
Nikto
Nikto is an Open Source web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be automatically updated.
Install this tool on kali
#sudo apt-get install nikto
#sudo apt-get upgrade
Nikto scan and check vulnerability on a web server.
Example:
#nikto -h http://192.168.1.19/virtualdirectory/index.html
Nbtstat
Nbtstat Displays NetBIOS over TCP/IP (NetBT) protocol statistics, NetBIOS name tables for both the local computer and remote computers, and the NetBIOS name cache. nbtstat allows a refresh of the NetBIOS name cache and the names registered with Windows Internet Name Service (WINS).
Run on Windows-based command prompt
#nbtstat -a 192.168.1.150
nbtstat can find a mac address on the same network systems.
Try this list of tools for Penetration test
- driftnet – (capture pakcet audio and images from network- sniffing tool)
- etherape – (visually monitor networks)
- nslookup – ( dns information )
- macof – (flooding mac address to busy traffic)
- SMAC – ( windows tool to change mac address)
- tshark – ( kali linux tool analyze network traffic)
- pwdump – ( get password for remote system)
- pstools – ( list of windows tools)
- fport – (find open port)
- netdiscover – ( packet capture)
- superscan 4 – ( scan target pc open ports)
- urlsnarf – (kali tool sniff http request)
- wwwstat – ( view website details)
- webspy – (kali tool sniff url realtime)
- tini.exe – (telnet torjan)
