Sonicwall Firewall – All detailed configuration steps.
Here I’m talking about SonicWALL TZ670 Series firewall Entry Level Next-Generation Firewall.
The SonicWall TZ670 is the first desktop-form-factor next-generation firewall (NGFW) with 10 Gigabit Ethernet interfaces

Features of TZ670
- 10 GbE interfaces in a desktop form factor
- SD-Branch ready
- Secure SD-WAN capability
- SonicExpress App onboarding
- Zero-Touch Deployment
- Single-pane-of-glass-management through cloud or firewall
- SonicWall Switch, SonicWave Access Point and Capture Client integration
- Built-in and expandable storage
- Redundant power
- High port density
- Cellular failover
- SonicOS 7.0
- TLS 1.3 support
- Groundbreaking
- performance
- High connection count
- Fast DPI performance
- Low TCO
Register the Device
Registration: Go to https://cloud.sonicwall.com
You have to create a account on this site then go to My SonicWALL -My Workspace – Register Products – add all the details about the device serial number and authorization code from the back side of the box.
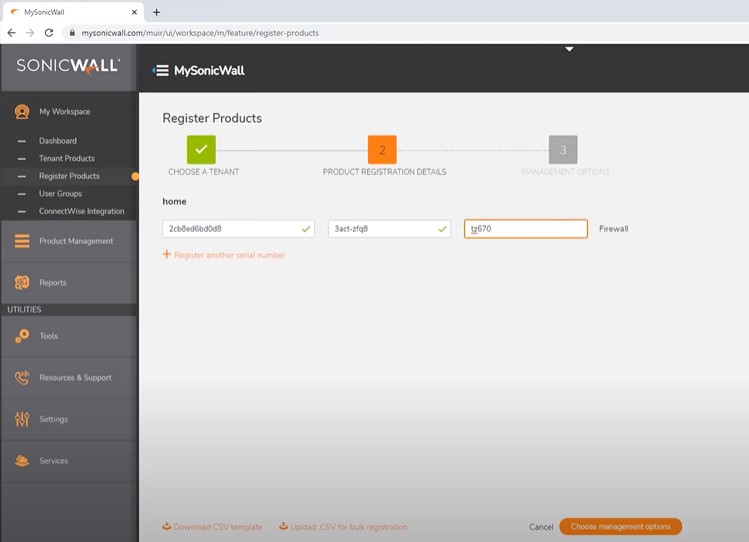
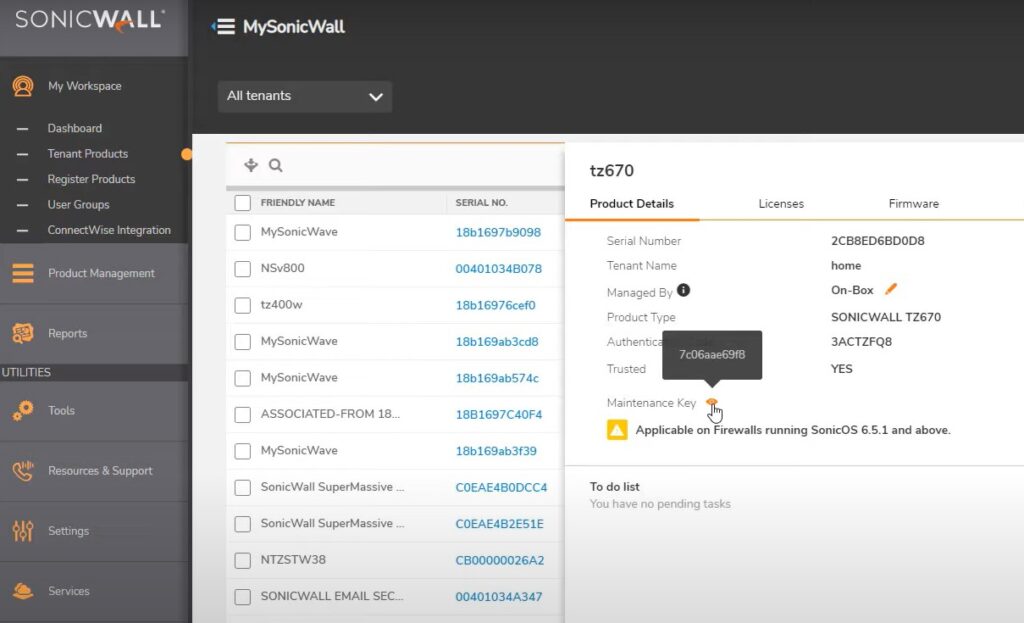
Depends on your license manage firewall on 3 ways. 1.Cloud, 2.On-Prem and 3.On-Box.
Always remember Maintenance key on the firewall – Incase required reboot the firewall on safe mode this code is required.
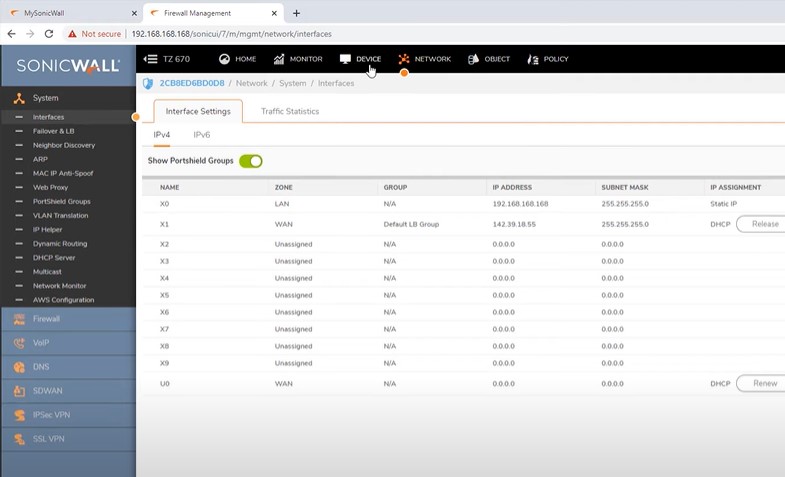
First connect device on LAN network and bootup firewall with default settings.
Default IP address: 192.168.168.168
Default username and Password: Admin / Admin
Now connect internet line on WAN port (X1).
Make sure that getting public ip address from WAN network.
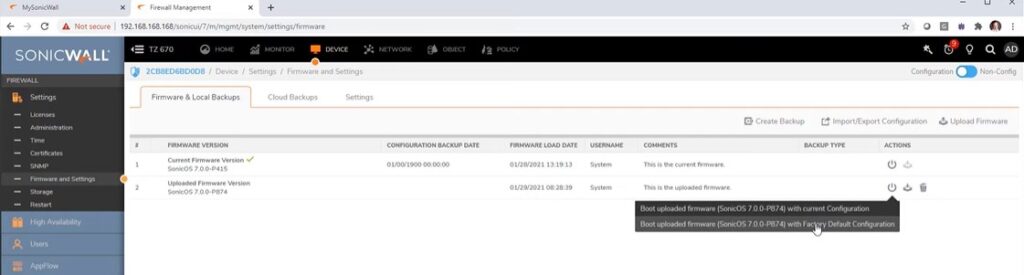
Device Registration: login to Mysonicwall section using your Cloud login credentials.
Device /Settings / Licenses
Upgrade latest firmware from SonicWall site.
SonicOS version 7.0
On Device -> Fireware & local Backups -> Actions -> Boot updated firewire with current configuration.
Link Aggregation on Sonicwall
I have divided Lan network to Three Zones.
- Main LAN network
- Store network (Isolated from main network)
- Wifi Network ( Vlan supported and Guest wifi)
Dhcp IP scope for three zones:
Main network: 192.168.10.0
Store network: 172.16.0.0
Public Wifi Network: 10.10.10.0
Main network Zone already created with default ip range.
Store Network Zone Creation:
Go to Object -> Main Objects -> Zones
Custom Zone creation for isolation network interface from main network.
While creating zone disable all the default settings and put name and security type ” Trusted”
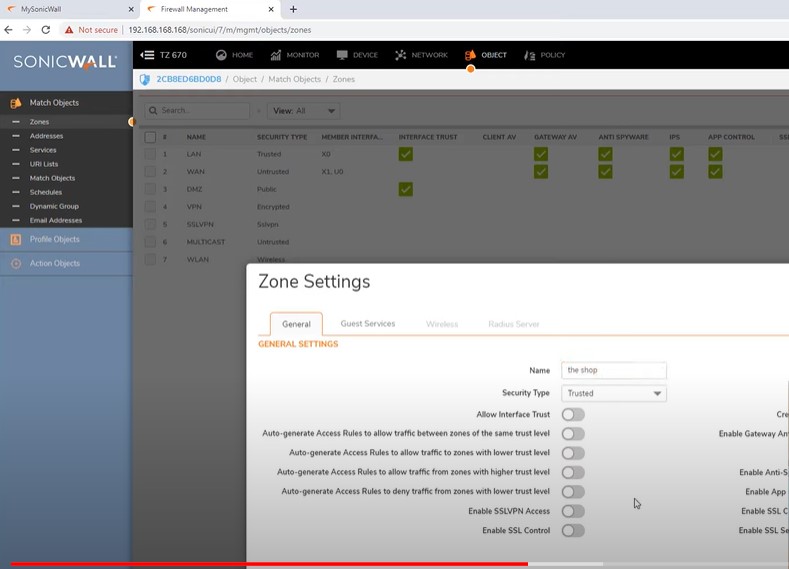
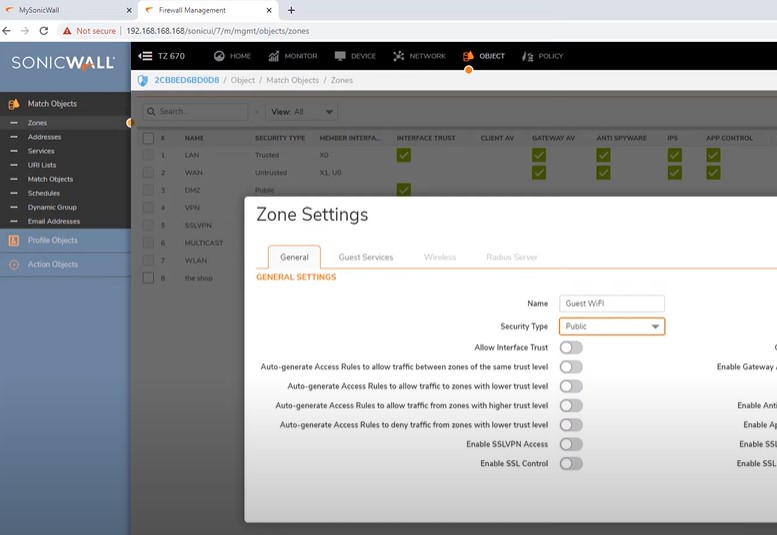
Zone creation for Public Guest wifi
Name: Guest wifi
Security type: Public
Disable all the below settings.
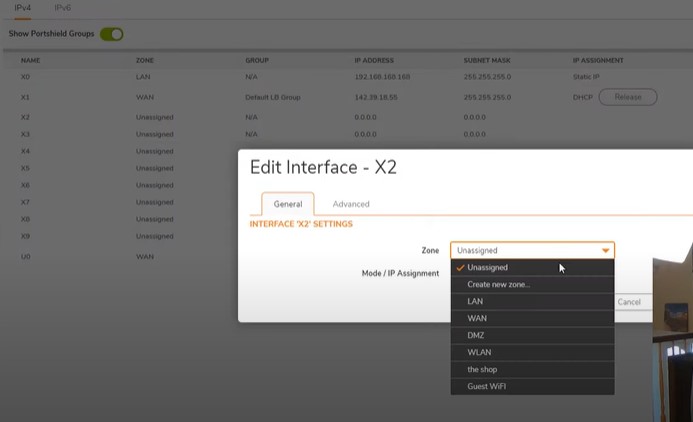
Network interface assign to Zones
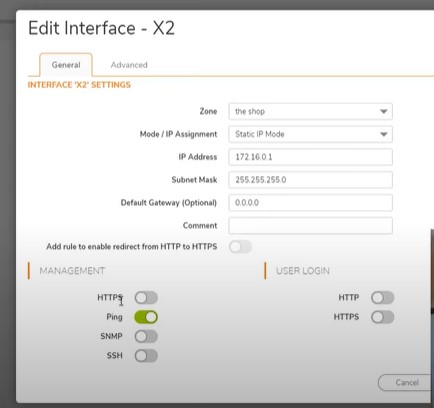
Assign network interface X2 to Zone “The shop”
Go to -> Network -Add Interface -General Tab
Zone: The shop
Mode / IP assignment: Static IP mode
IP address: 172.16.0.1
Subnet Mask: 255.255.255.0
Default Gateway: 0.0.0.0
Only allow ping because don’t allow access to firewall from Store network.
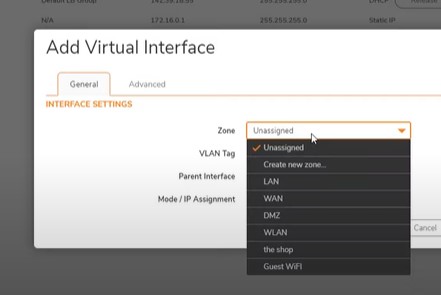
Add Virtual interface for Wifi VLAN
Main network vlan: 100
Store network vlan: 200
Wifi netwrok vlan: 300
Assign Wireless Access point assigned to X3 port. Allow main network and store network access through vlan
Consider main network vlan: 100 and Store network Vlan: 200 for identification wireless network.
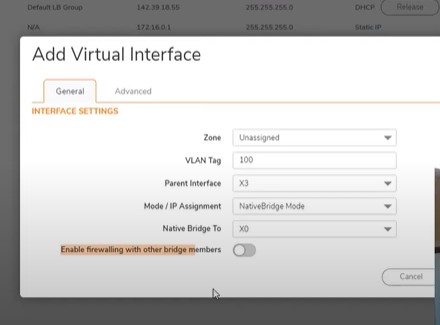
X3 port connect to Main network : First add virtual interface
Zone: Unassigned
Vlan Tag: 100
Parent interface: X3
Mode: Static IP Mode
IP address: NativeBride mode (Directly connected Main network and get ip address same)
Native Bridge To: X0 (Connect to X0 Lan interface)
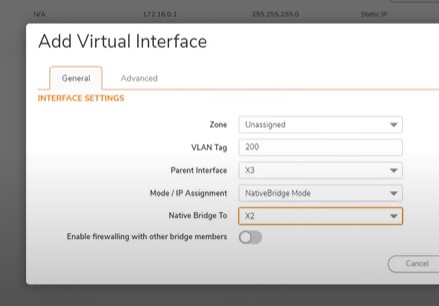
Same for store network on above Allow Store network on Wireless using Vlan 200
Zone: unassigned
Vlan Tag: 200
Parent interface: X3
MOde: NativeBridge mode
Native Bridge To: X2 (Connect to X2 store network interface)
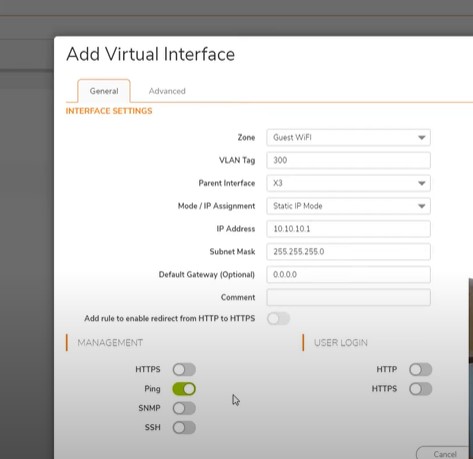
Guest Wifi Vlan 300 – Separated from all the network and different ip range
Add Virtual interface:
Zone: Guest wifi
Vlan Tag: 300
Parent interface: X3
Mode: Static IP Mode
IP address: 10.10.10.1
Subnet mask: 255.255.255.0
Default gateway: 0.0.0.0
Managment: Ping allow
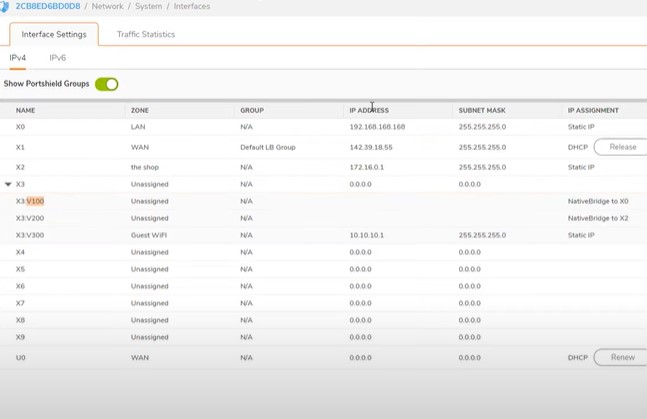
Overall interface
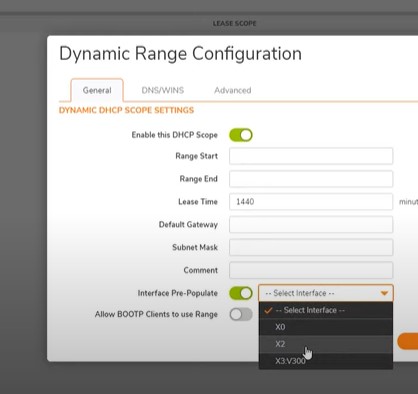
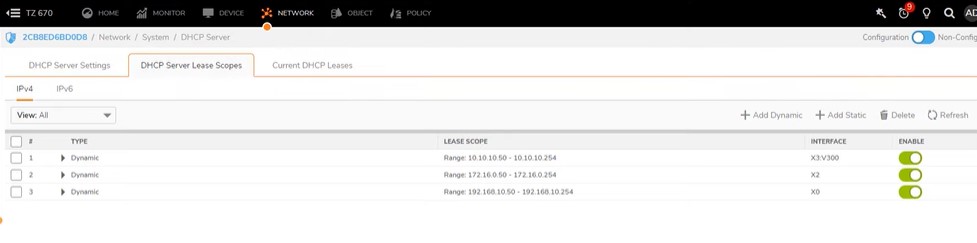
Set Dhcp server for Store and wifi network
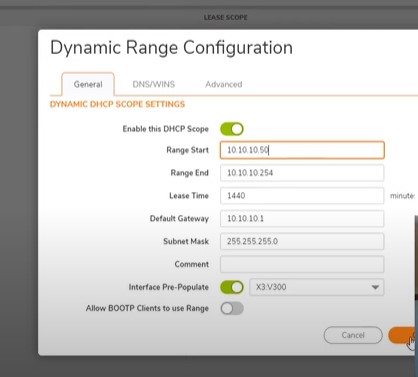
Go to Dashboard- System- Dhcp server – DHCP Serer Lease Scopes- Add Dynamic range
General Tab- Interface Pre-Populate enable and select the the port X2 – Automatically get ip address range
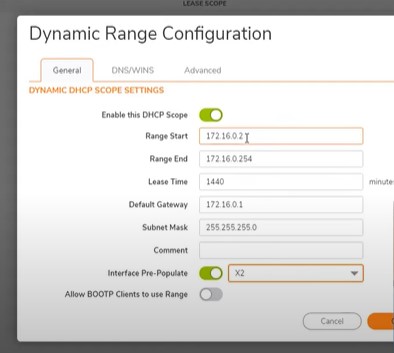
Same steps for wifi- Add Dynamic range- Interface pre-populate enable and select X3
Overall Dhcp server lease scopes
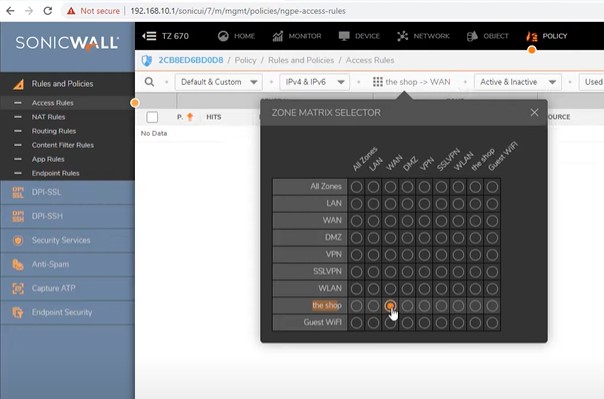
Policy Allow internet connection
Policy must allow Shop and wifi network access to WAN network.
Dashboard -> Policy -> Select shop to Wan zone matrix – Add
Allow source(any) to Destination(any) address and save settings
Same like Wifi netowork create policy and allow all access.
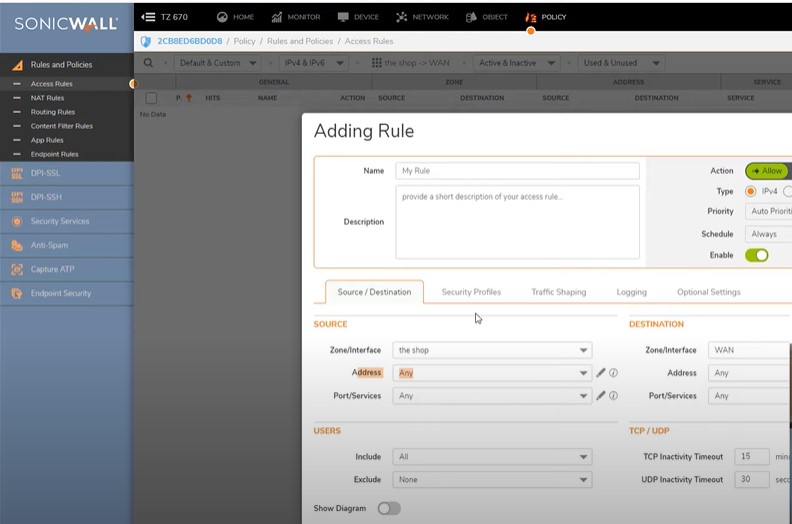
Customer complain that internet is working then make sure check the policy section everything is allowed.
Security Features Must Turn on Firewall
- Gateway Anti-Virus
- Anti-Spyware
- IPS
- Botnet filter
- App Control
- Content filter
- DPI – SSL
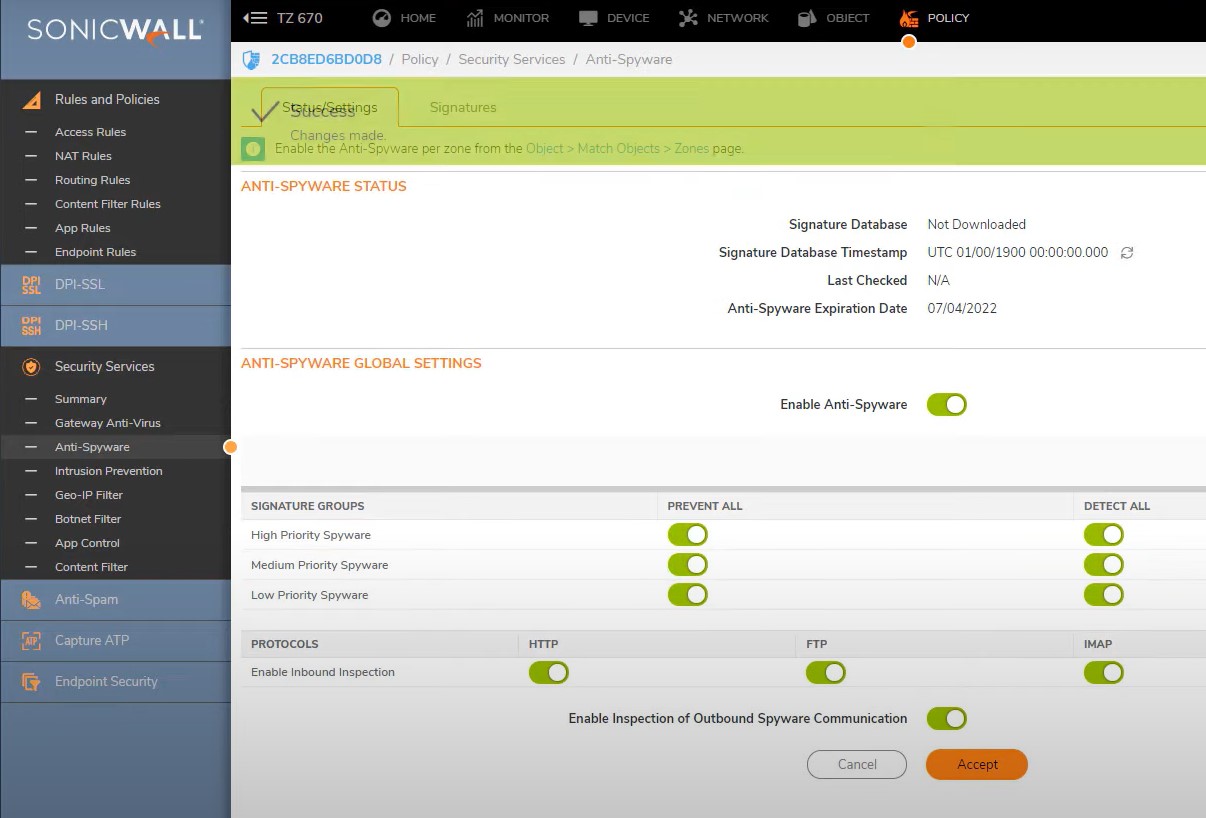
Gateway Anti-virus
Policy -> Security Services -> Gateway Anti-Virus
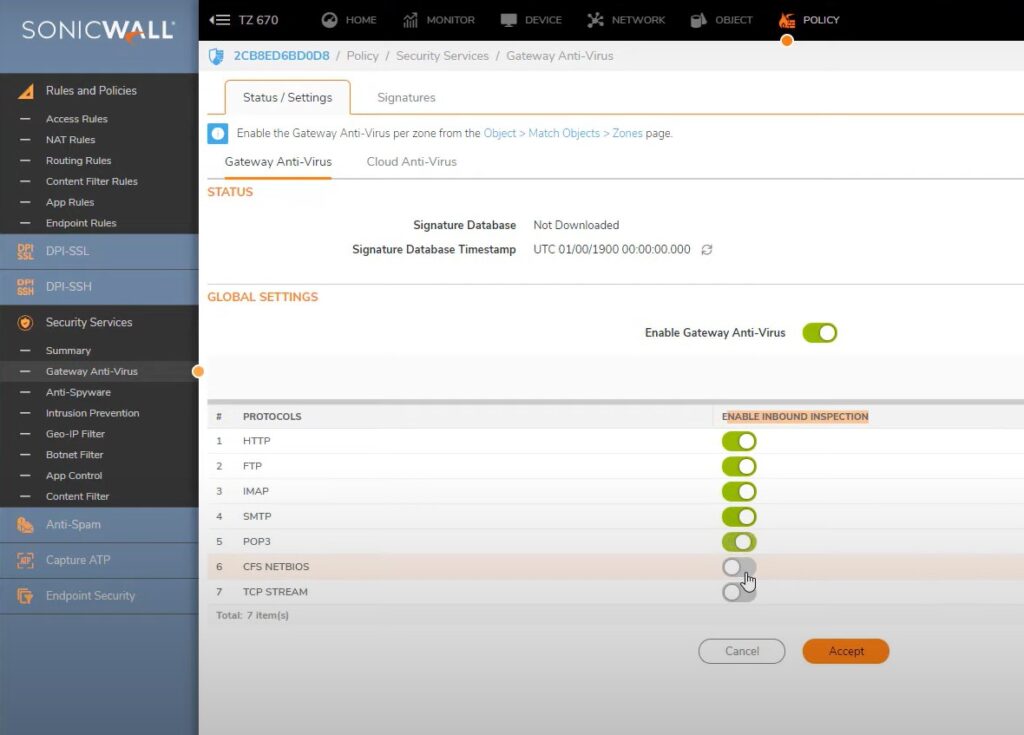
Enable the Gateway Antivirus per zone
Object ->Match Objects ->Zones
Check Lan network check Gateway anti-virus enabled or not
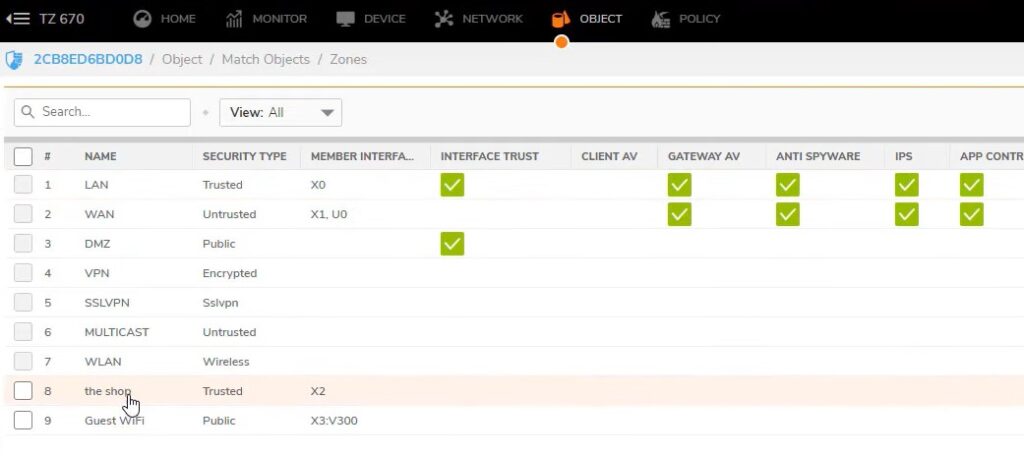
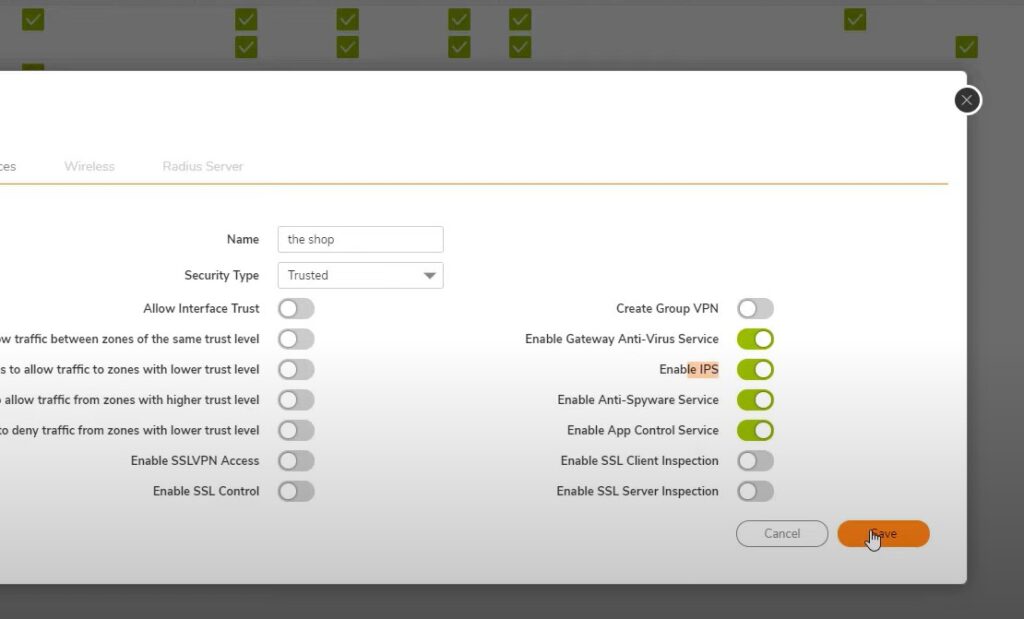
Go to store zone – enable all security features
1. Enable Gateway Anti-Virus Service
2. Enable IPS
3. Enable Anti-Spyware Service
4. Enable App Control Service
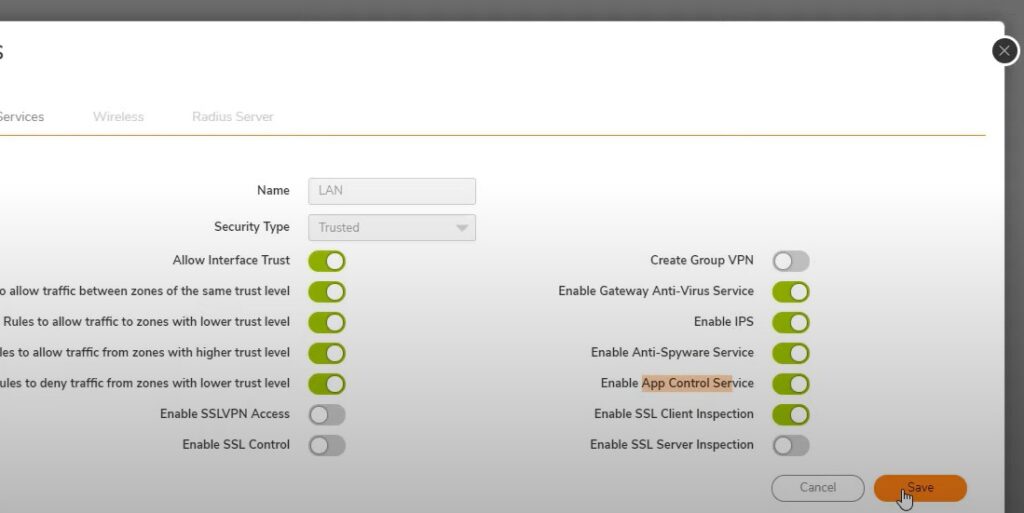
Guest wifi network – Better don’t turn ON all the features because of its out of scope
Now to go to Policy -> Security Services -> Gateway Anti-Virus
Enable all the featues of Gateway Anti-Virus

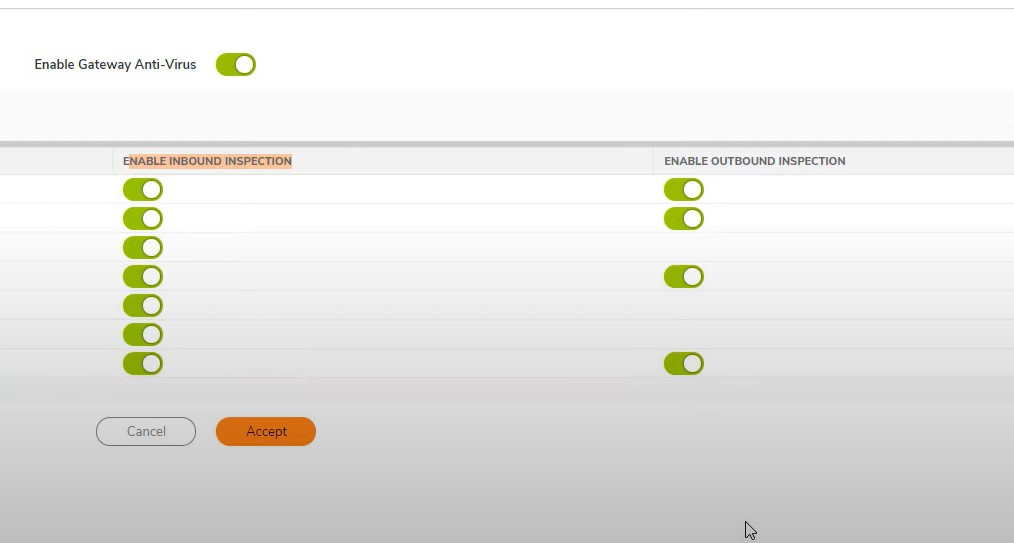
Turn ON Anti-Spyware -> prevent and detect all enable
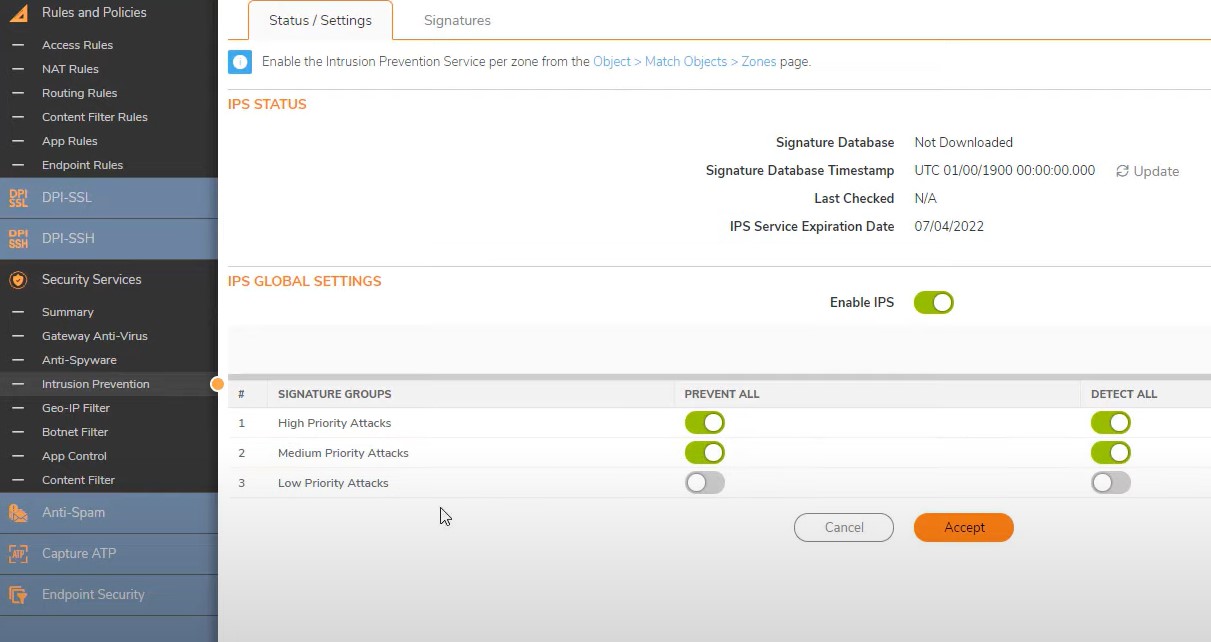
Enable IPS -> prevent and detect all enable
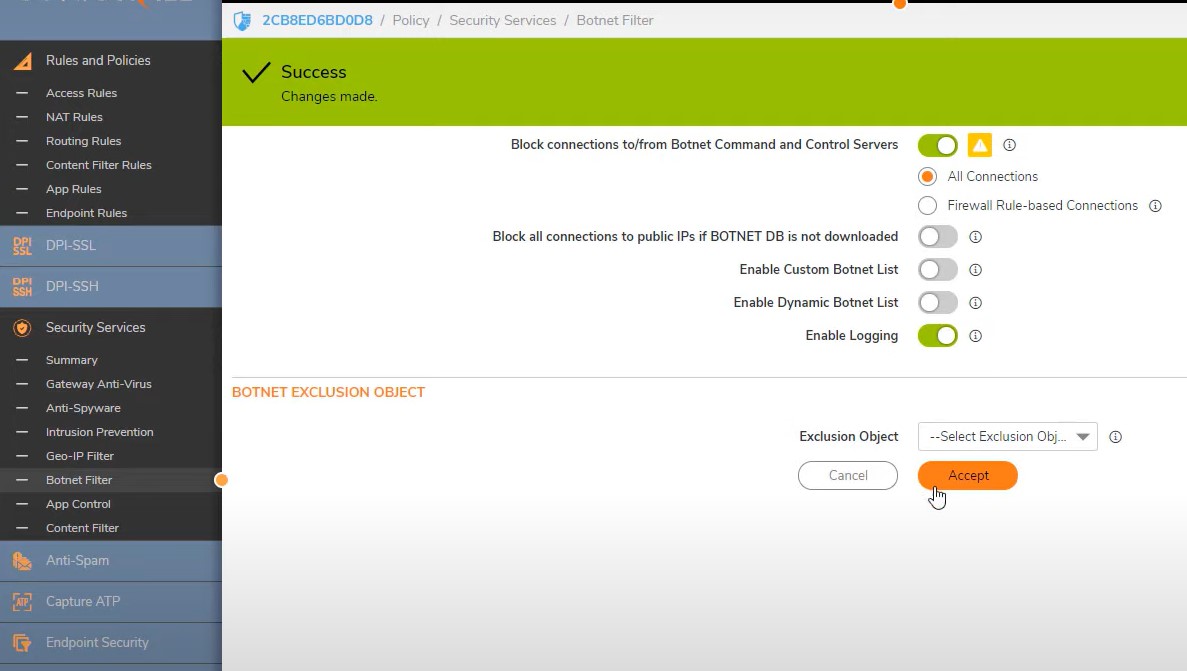
Turn on Botnet Filter -> Block connection and enable logging
Turn on App Control -> Block connection and enable logging
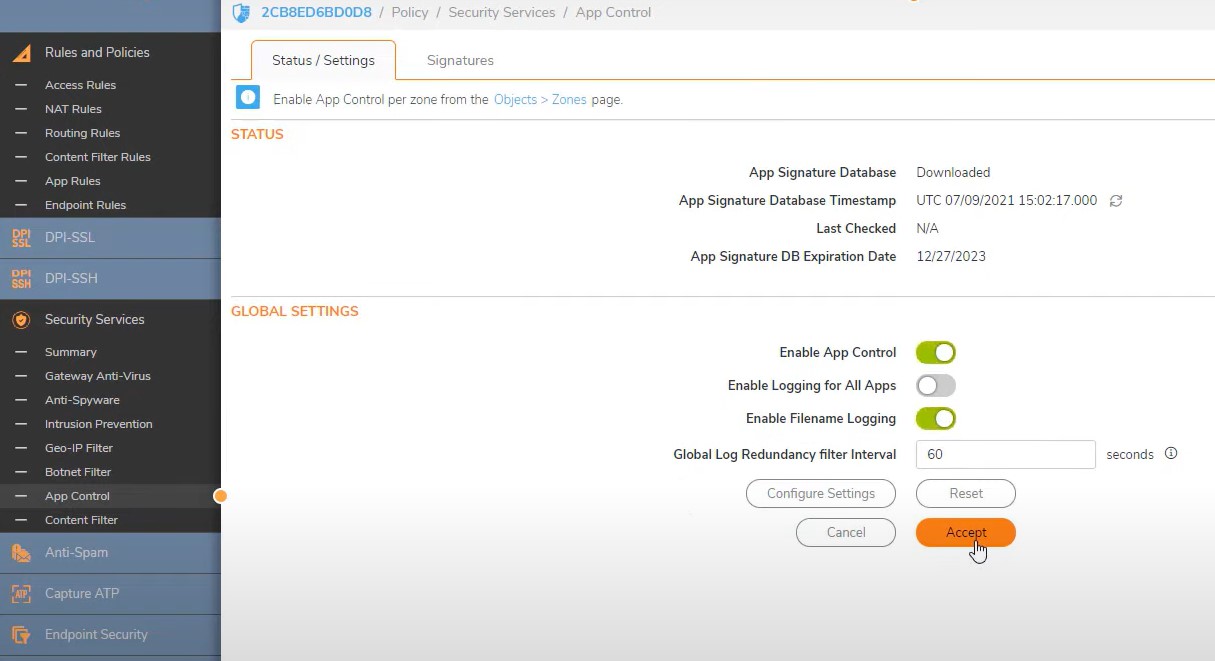
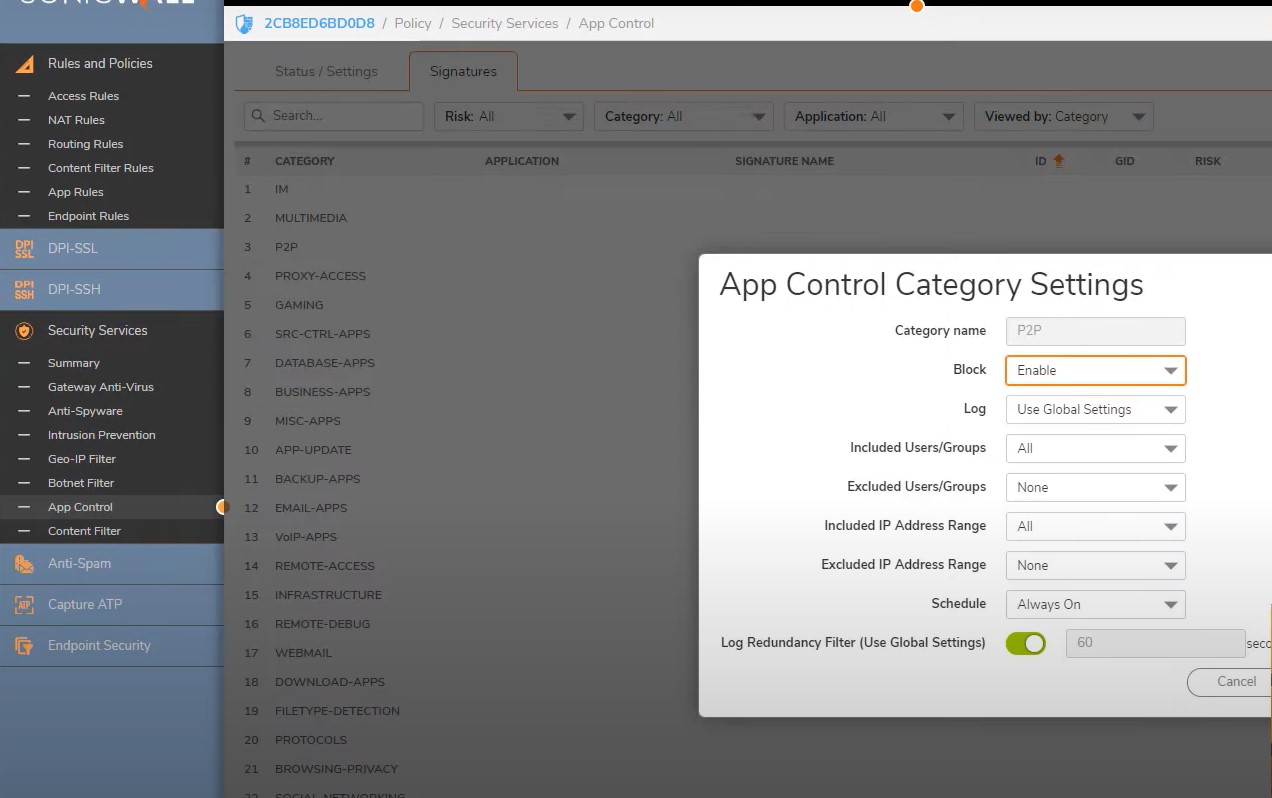
Signature tab -> View by Category -> P2P -> Enable block and Save
Enable Content Filter -> to configure go to Rules and Policies -> Content Filter Rules
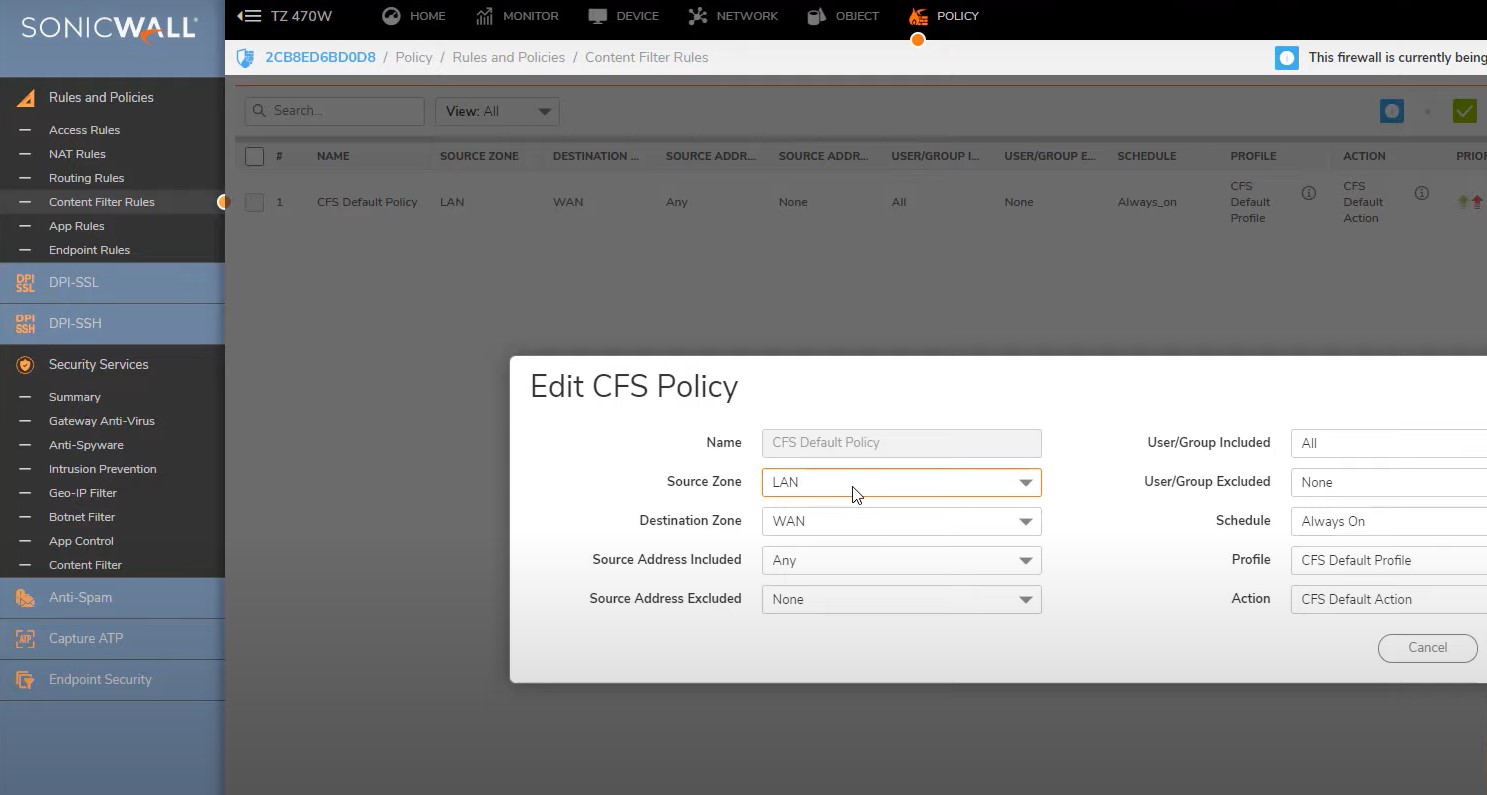
Before creating this rules you should have profile and content action items are ready.
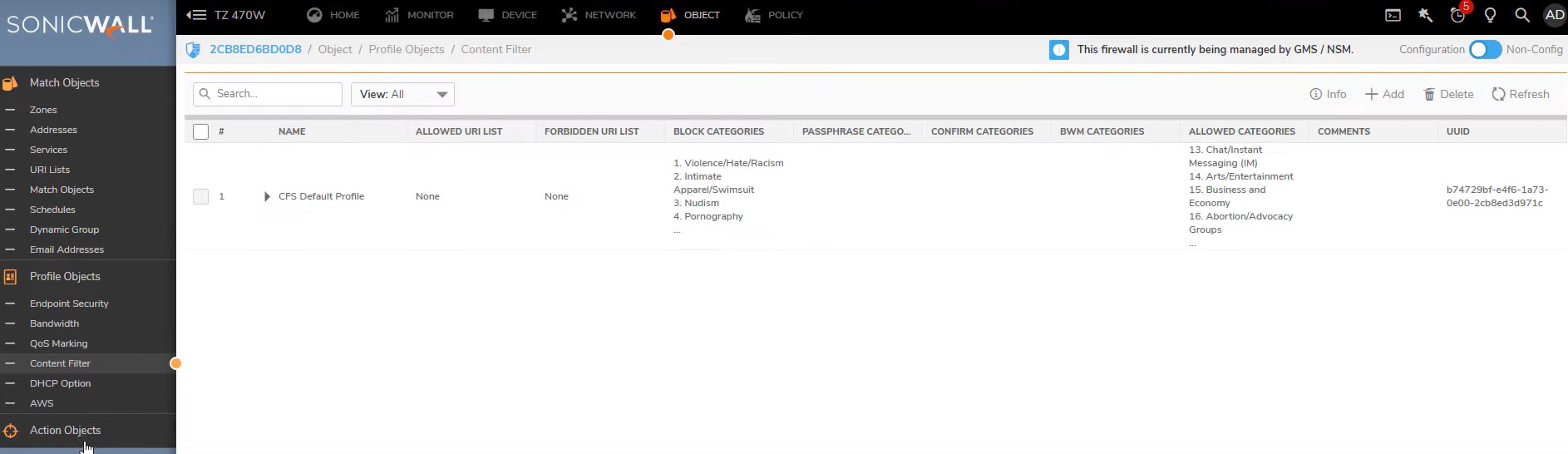
Checking Content filter profile -> Go to Object -> Profile Objects ->Content filter
Open that profile select category configuration -> Block approparate section
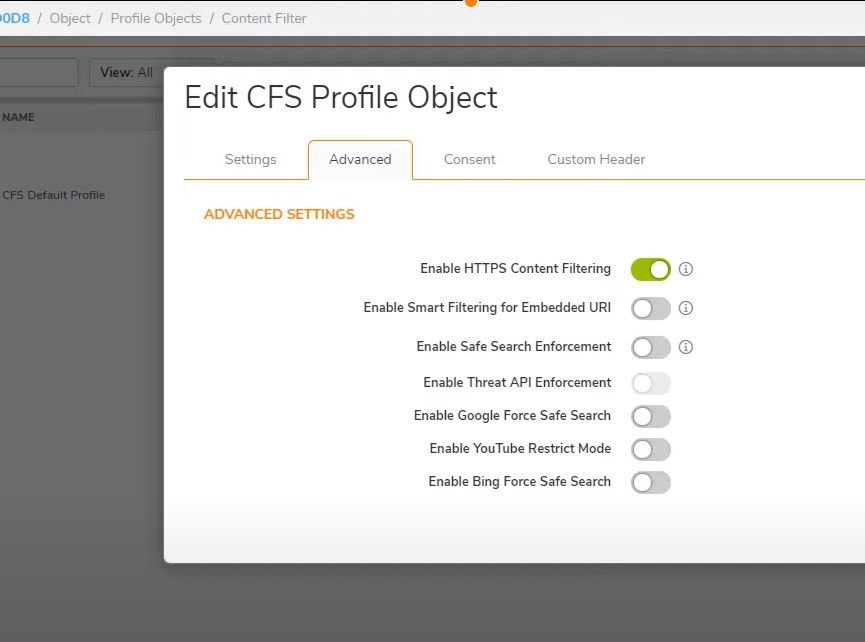
Advanced section – Enable https content filter traffic
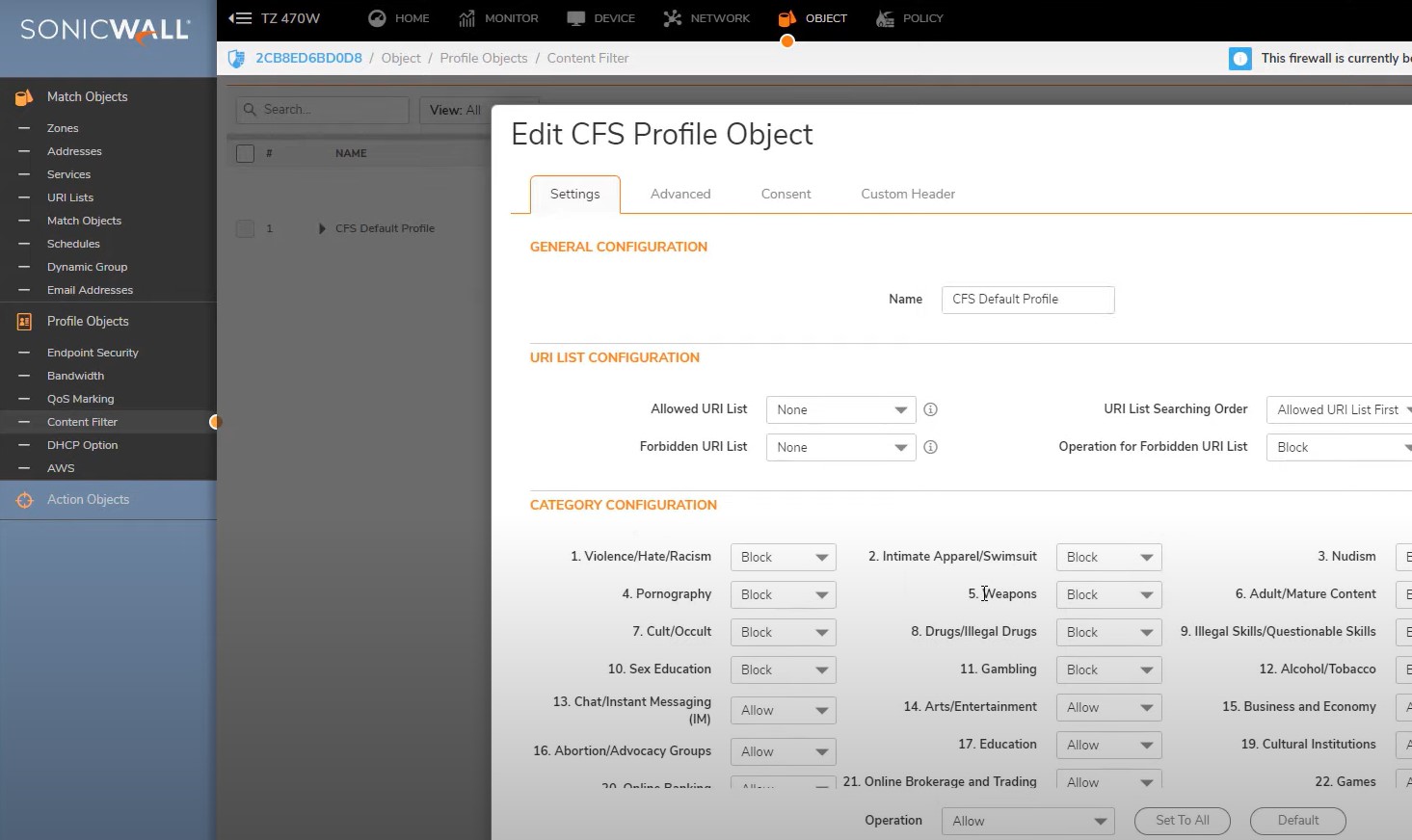
Advanced section – Enable https content filter traffic
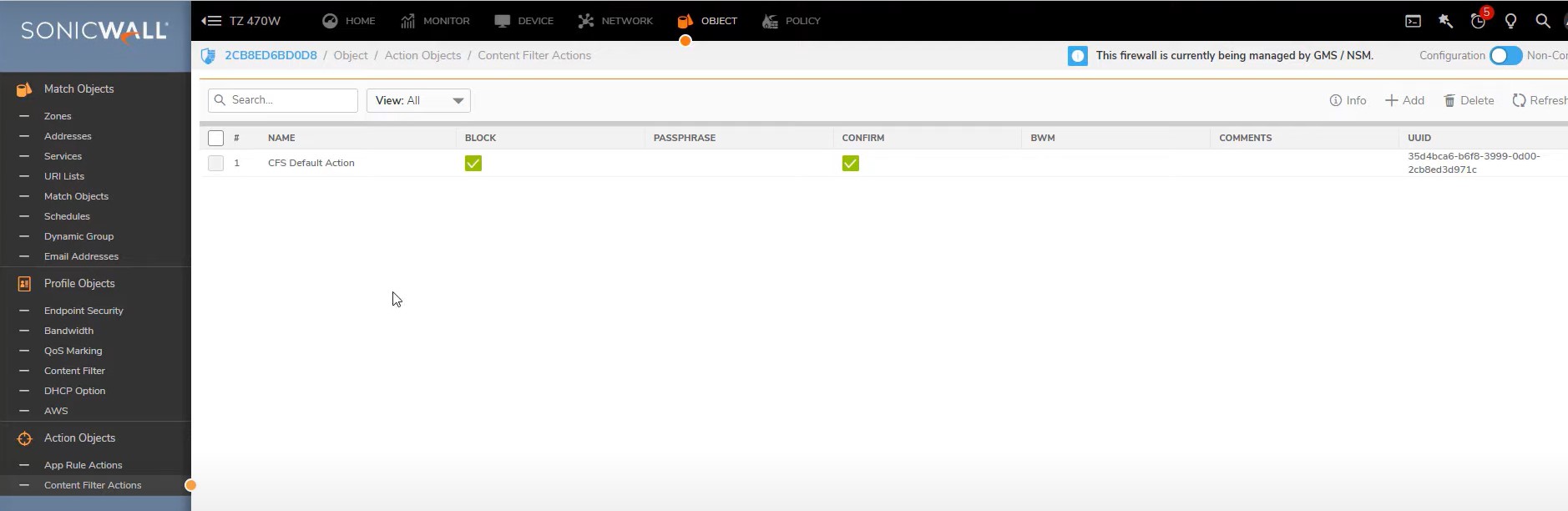
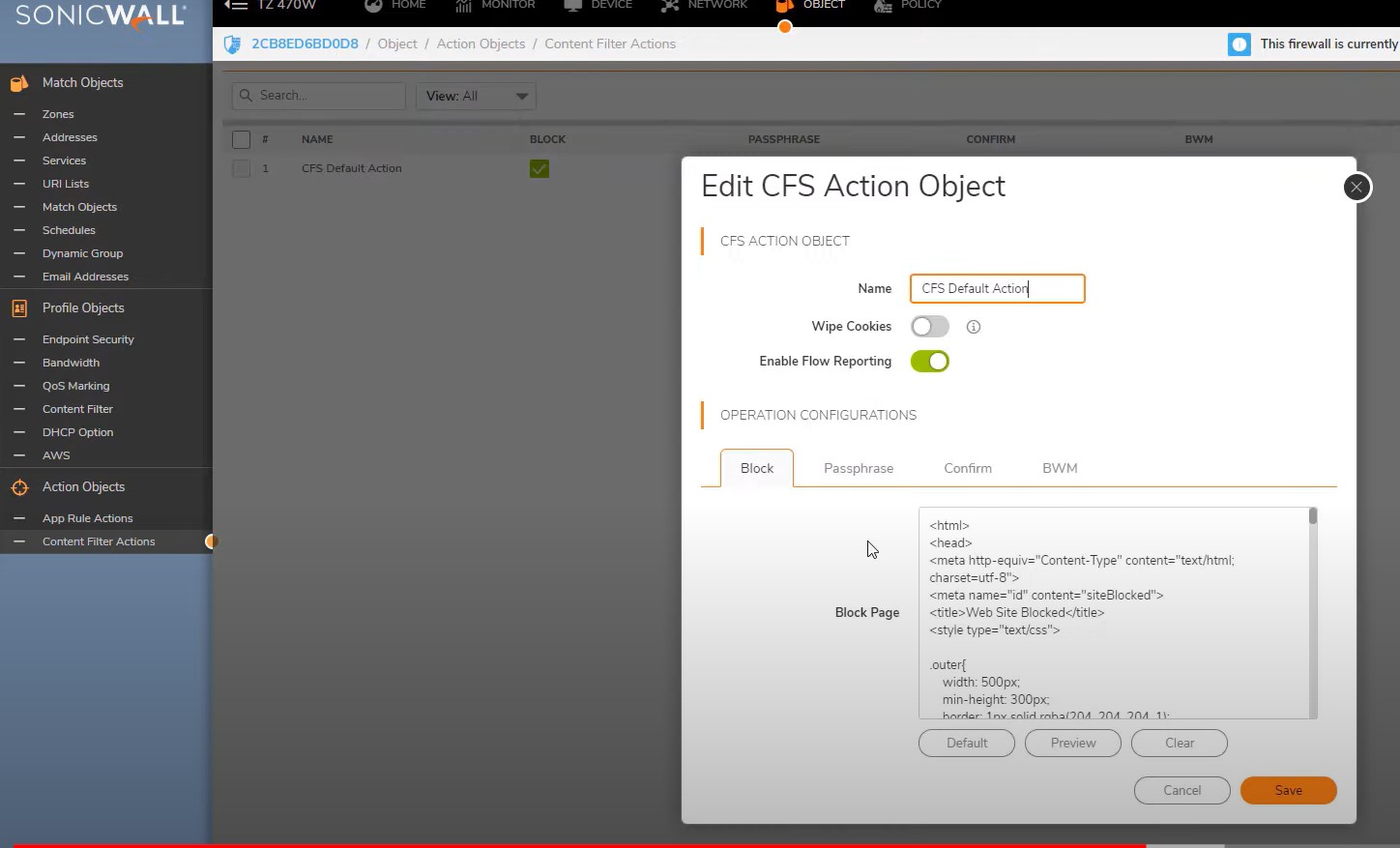
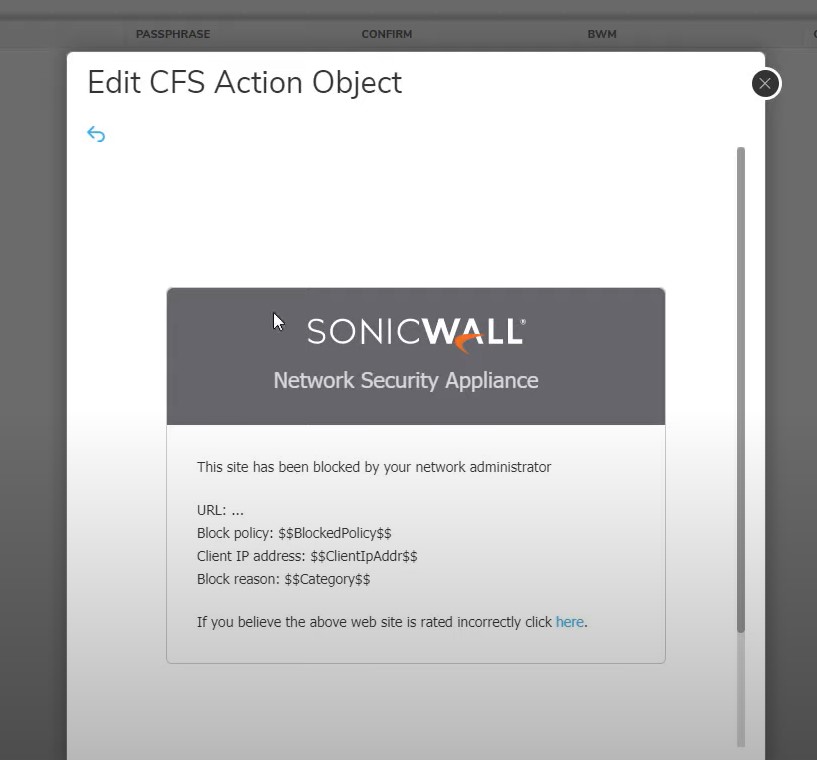
Editing block message go to Content filter Actions -> Action Object -> Contents filter Actions
Html page you choose to edit content and display
BWM – Bandwidth management
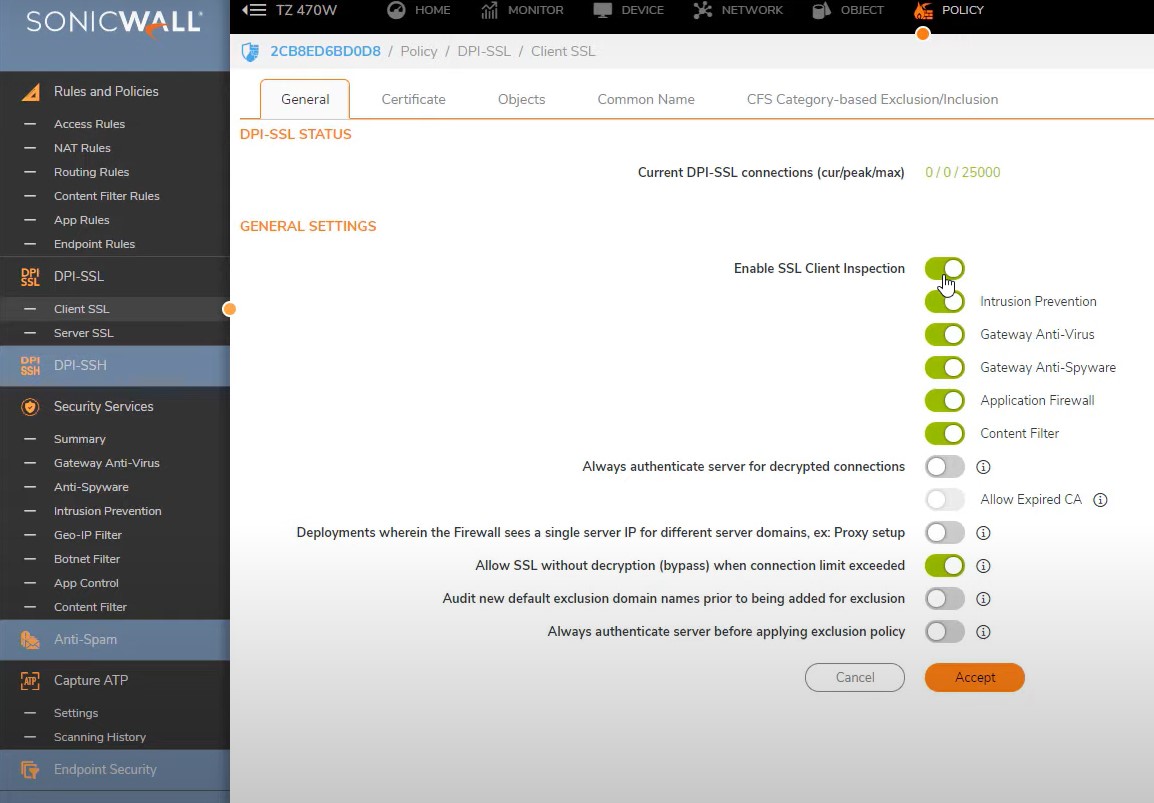
DPI-SSL enable client side ssl
encrypted ssl connection will inspect from firewall
SonicWall SD-WAN Configuration
SD-WAN (Software-Defined Wide Area Network) is a technology that uses Software-defined networking (SDN) concepts to provide software-based control over wide area network connection. It enables distributed organizations to build, operate and manage high-performance networks using readily-available, low-cost public Internet services. An alternative to more expensive technologies such as MPLS, Secure SD-WAN allows retailers, banks, manufacturers and other organizations to connect sites spread over great distances for the purpose of sharing data, applications and services. Features such as intelligent Failover, load balancing help ensure more consistent performance and availability of critical business and SaaS applications.
SonicOS SD-WAN offers these features:
- Application-aware routing
- Dynamic path selection based on Latency, jitter, and/or packet loss
- User-defined thresholds for quality assessment
- SD-WAN Interface Groups for WAN and VPN Numbered Tunnel Interface
- Path Performance Probes for metrics
- Connection-based traffic distribution
- Automatic connection Failover over VPN
- Provisioning and management (GMS and Capture Security Center)
- Zero-Touch Deployment firewall configuration
- Centralized management and policy configuration
- Analytics
For Example, Consider we have two offices
- Main office
- Remote office
Both office connected using SD-WAN Connection.
In Main office and Remote office we have following port configured Two WAN network and one VOIP connection.
Remote office firewall port connection
X1 (Blue)- 142.39.18.20
X2 (White)- 142.39.19.20
X3 (VOIP)- 172.16.7.0/24
Main office firewall port connection
X1 (Blue)- 142.39.18.30
X2 (White)- 142.39.19.30
X3 (VOIP)- 10.254.7.0/24
Now will configure Two vpn connection for fail over network.
- Blue vpn
- white vpn
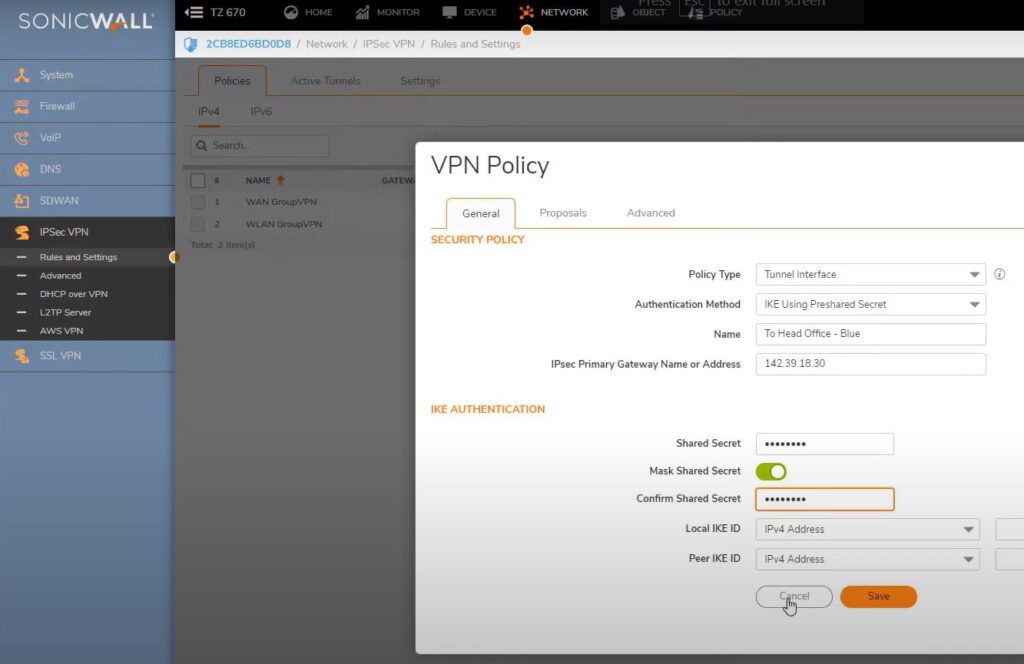
Create route based vpn on Remote office firewall – Blue VPN
Dashboard ->Network ->IPSec VPN ->Role and Settings ->Add
Policy type : Tunnel Interface
Authentication Method: IKE using preshared secret
Name: To Head office – Blue
IP Sec Primary Gateway Name or Address: 142.39.18.30
Shared Secret: lostlife@2020
Mark shared Secret: ON
Confirmed shared secreat: lostlife@2020
Local IKE ID: no changes
Peer IKE ID: no changes
Keep all settings same and no changes
SAVE
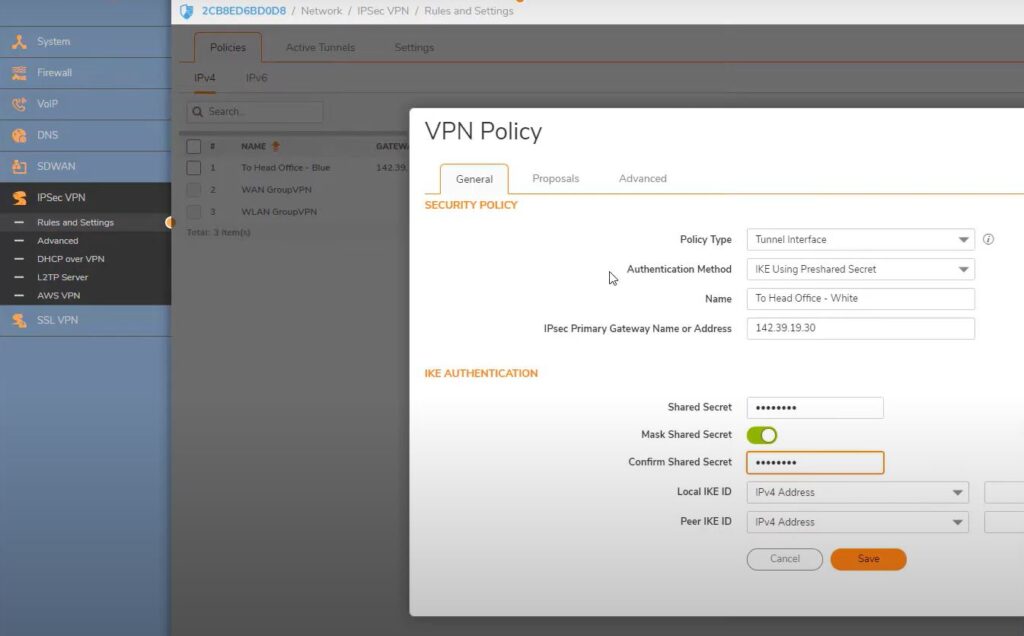
Remote office firewall – White VPN
Dashboard ->Network ->IPSec VPN ->Role and Settings ->Add
Policy type : Tunnel Interface
Authentication Method: IKE using preshared secret
Name: To Head office – White
IP Sec Primary Gateway Name or Address: 142.39.19.30
Shared Secret: lostlife@2020
Mark shared Secret: ON
Confirmed shared secreat: lostlife@2020
Local IKE ID: no changes
Peer IKE ID: no changes
Go to advanced -> VPN Policy bound to -> Interface X2
Keep all settings same and no changes
SAVE
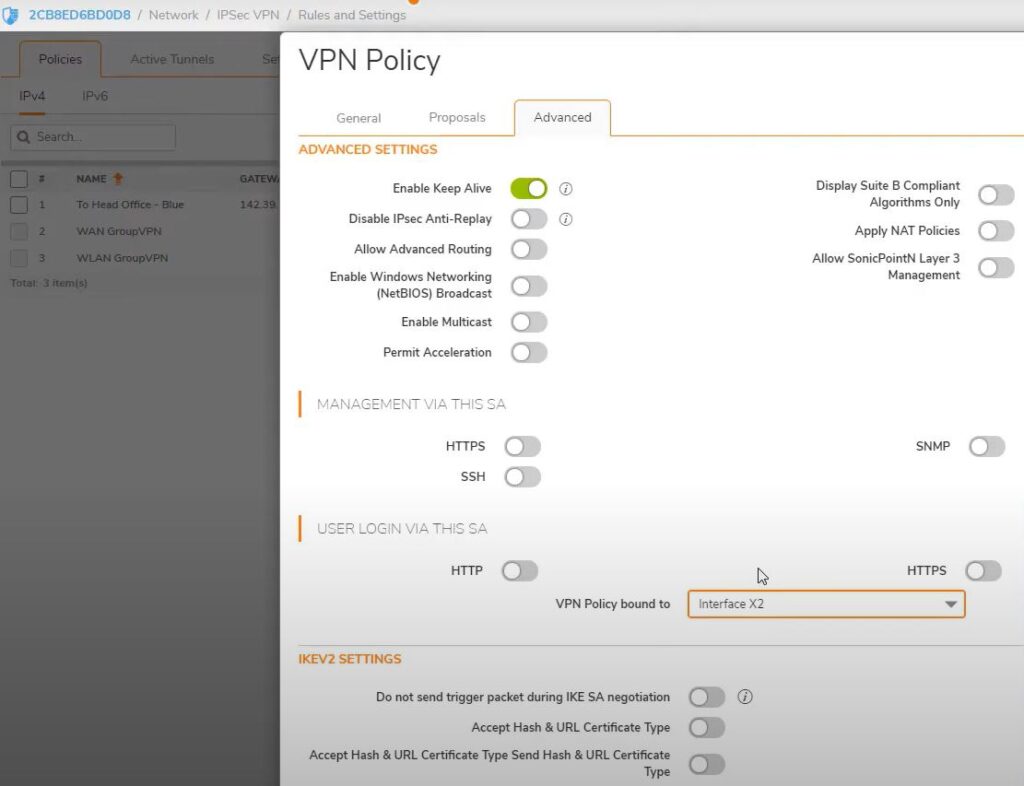
Overall Two ISP connection configured to Head office via VPN.
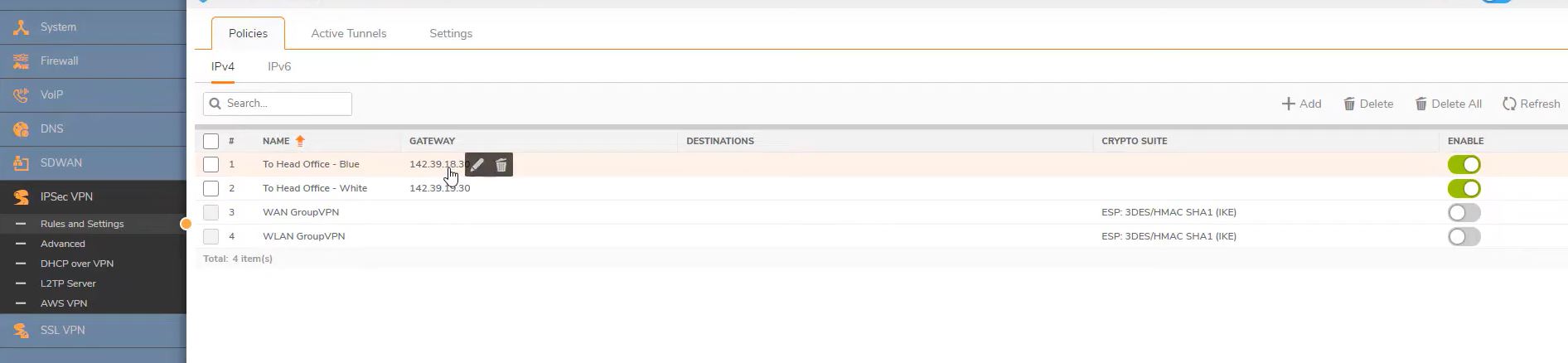
Now Configure on Main office firewall.
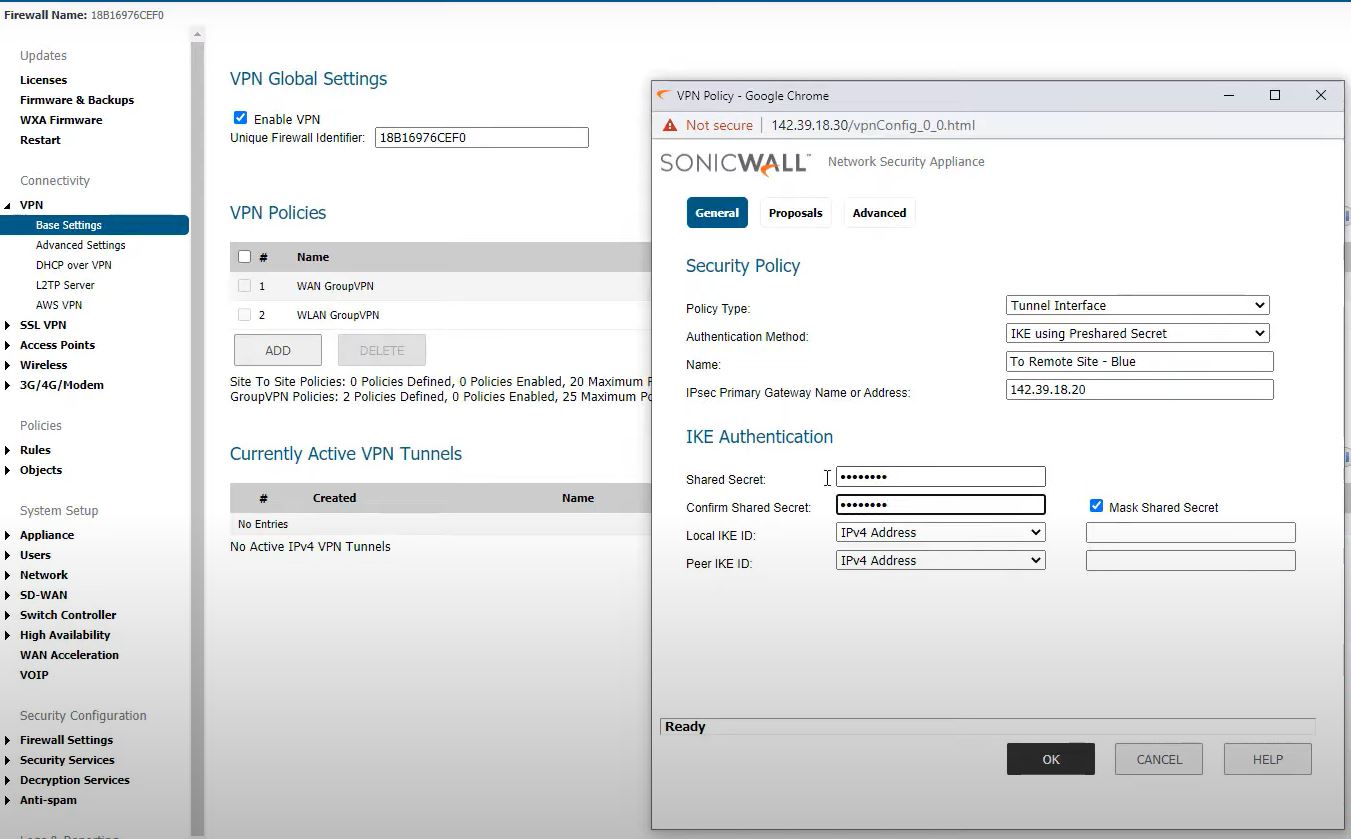
Main office firewall – Blue VPN
Settings information.
Policy type : Tunnel Interface
Authentication Method: IKE using preshared secret
Name: To Remote office – Blue
IP Sec Primary Gateway Name or Address: 142.39.18.20
Shared Secret: lostlife@2020
Mark shared Secret: ON
Confirmed shared secreat: lostlife@2020
Local IKE ID: no changes
Peer IKE ID: no changes
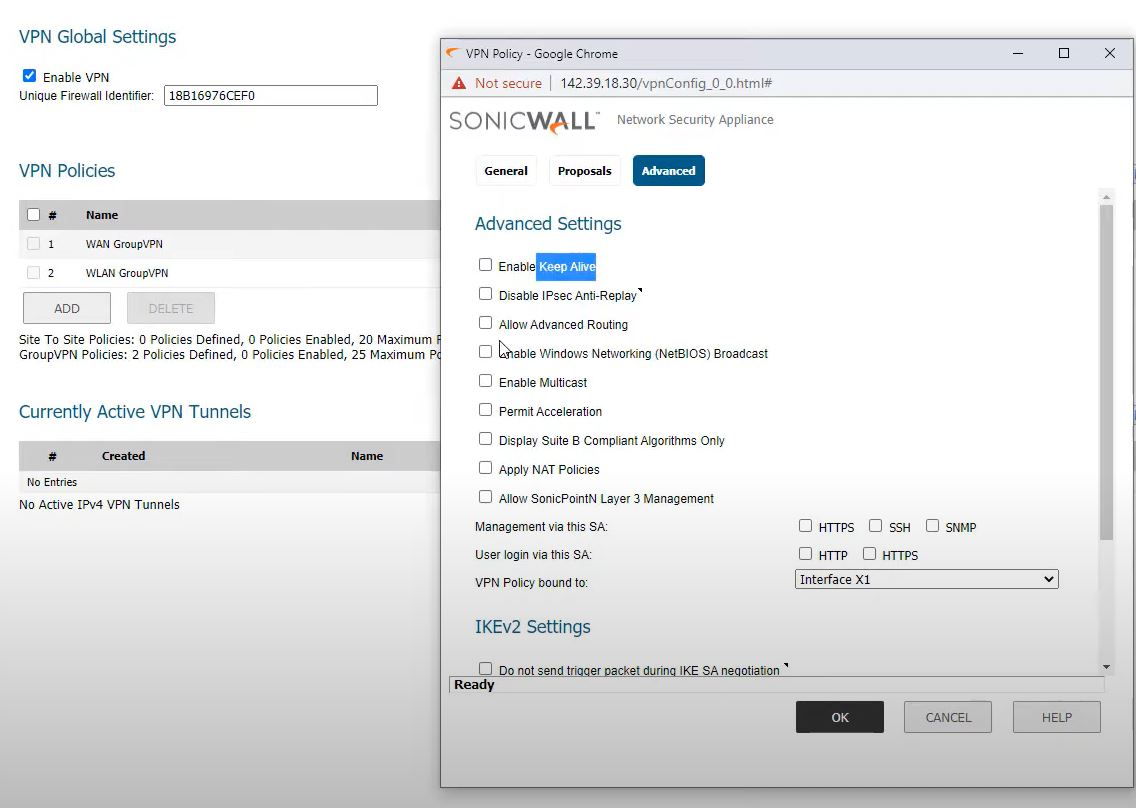
Go to advanced -> Enable keep alive-> Off
If remote site is ON keep then main office firewall should off.
Save.
If remote site is ON keep Alive then main office firewall should off that setting.
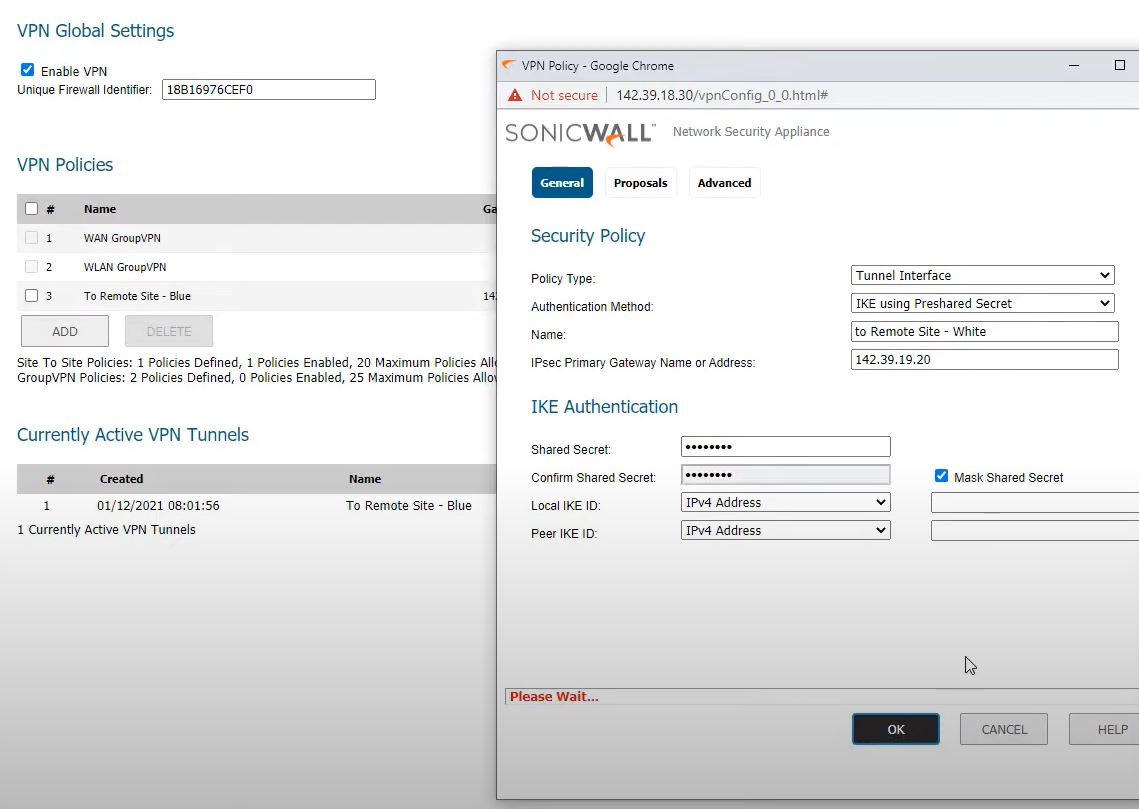
Main office Firewall- White VPN
Policy type : Tunnel Interface
Authentication Method: IKE using preshared secret
Name: To Remote office – White
IP Sec Primary Gateway Name or Address: 142.39.19.20
Shared Secret: lostlife@2020
Mark shared Secret: ON
Confirmed shared secreat: lostlife@2020
Local IKE ID: no changes
Peer IKE ID: no changes
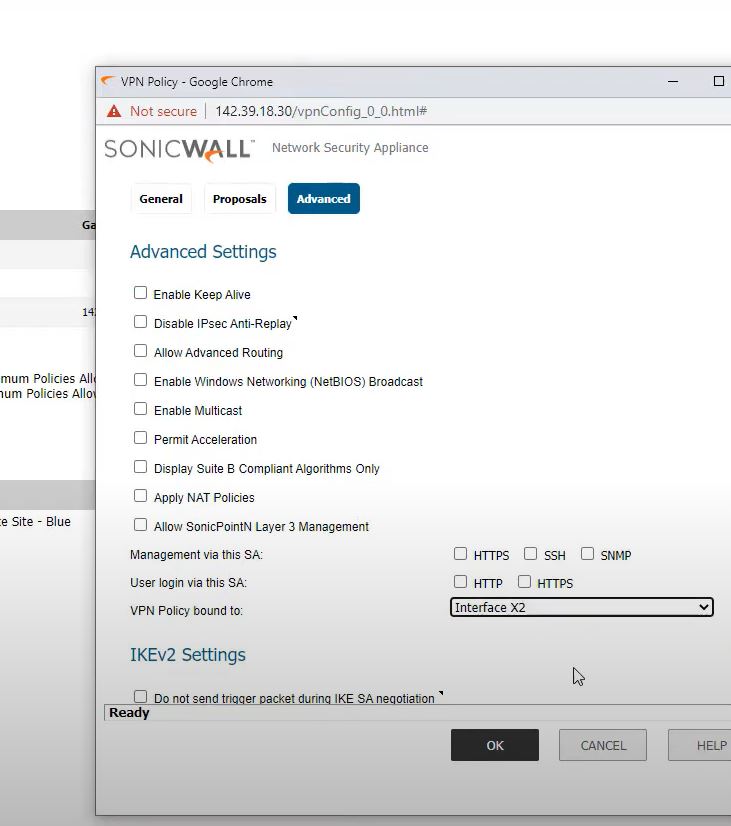
Go to advanced -> VPN Policy bound to -> Interface X2
Keep Alive -> OFF
Keep all settings same and no changes
SAVE
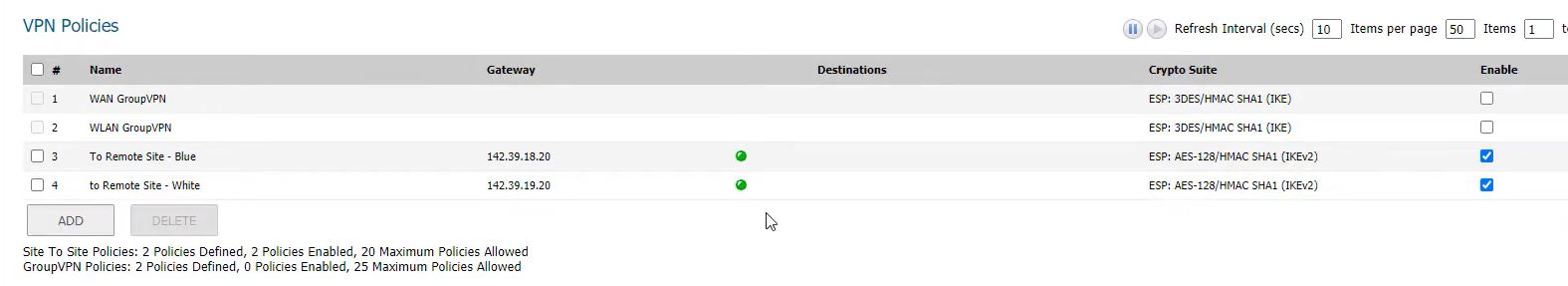
Overall connection in main office
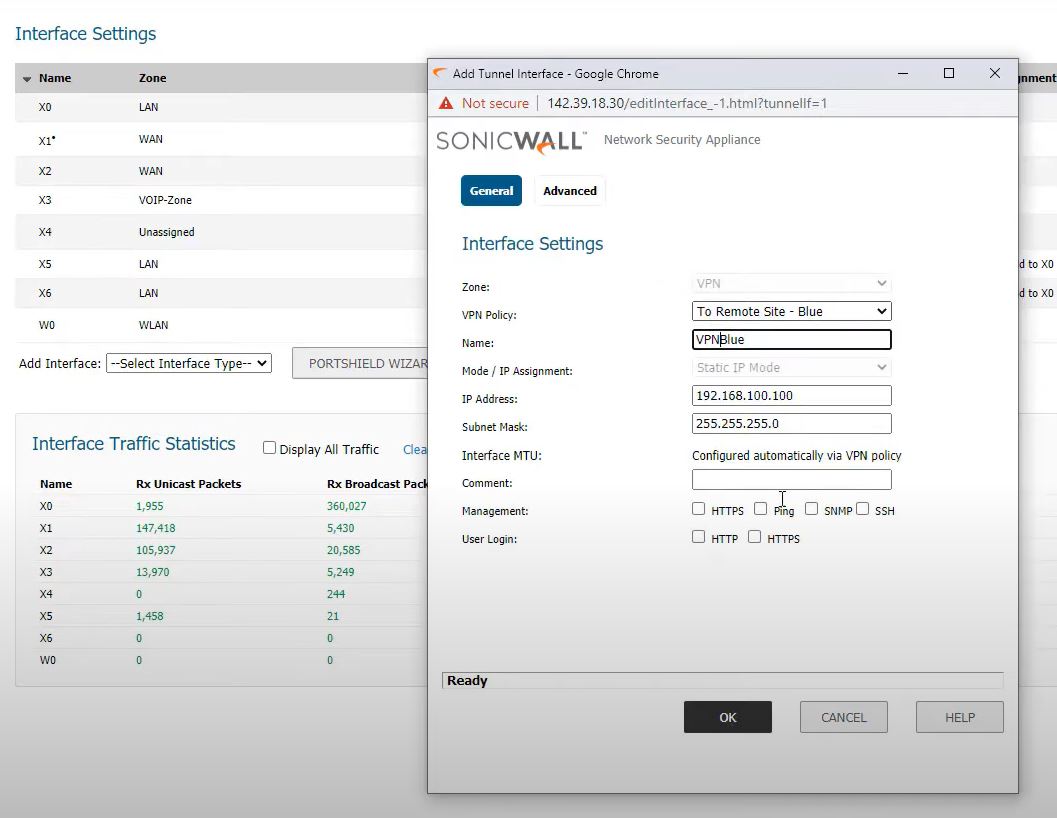
Creating VPN interface in Main office firewall for Blue
Dashboard ->Network->Interface->Add interface ->Add VPN Tunnel Interface
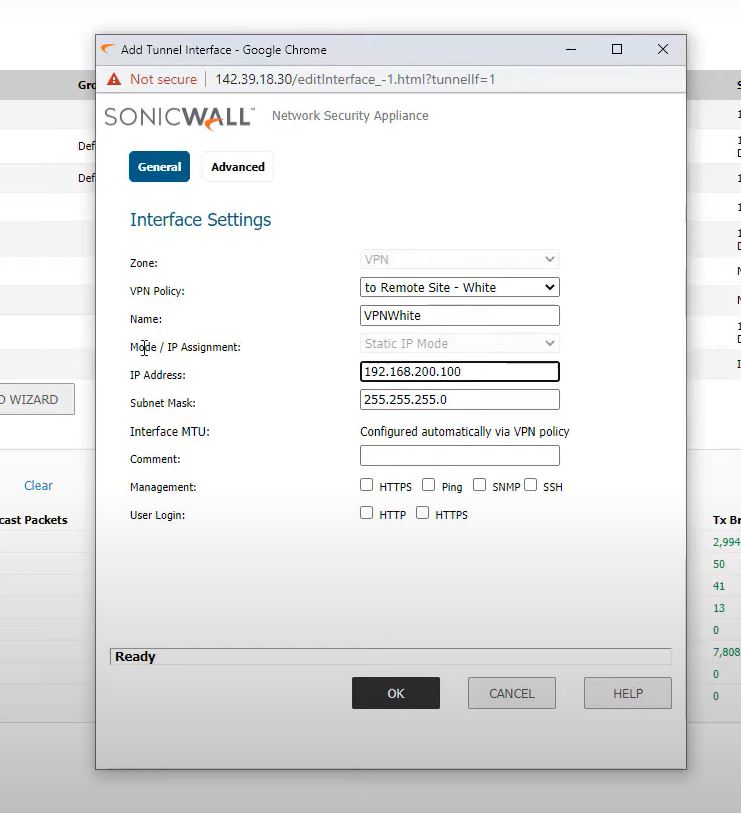
interface settings
Zone: VPN
VPN Policy: To Remote office – Blue
Name: VPNBlue
Model: Static IP Mode
IP Address: 192.168.100.100
Subnet Mask: 255.255.255.0
Inteface MTU: Configured Automatically via VPN Policy
Save
Same for White interface in Main office firewall
Creating VPN Interface in Main office Firewall- White
Dashboard ->Network->Interface->Add interface ->Add VPN Tunnel Interface
interface settings
Zone: VPN
VPN Policy: To Remote office – White
Name: VPNWhite
Model: Static IP Mode
IP Address: 192.168.200.100
Subnet Mask: 255.255.255.0
Inteface MTU: Configured Automatically via VPN Policy
Save
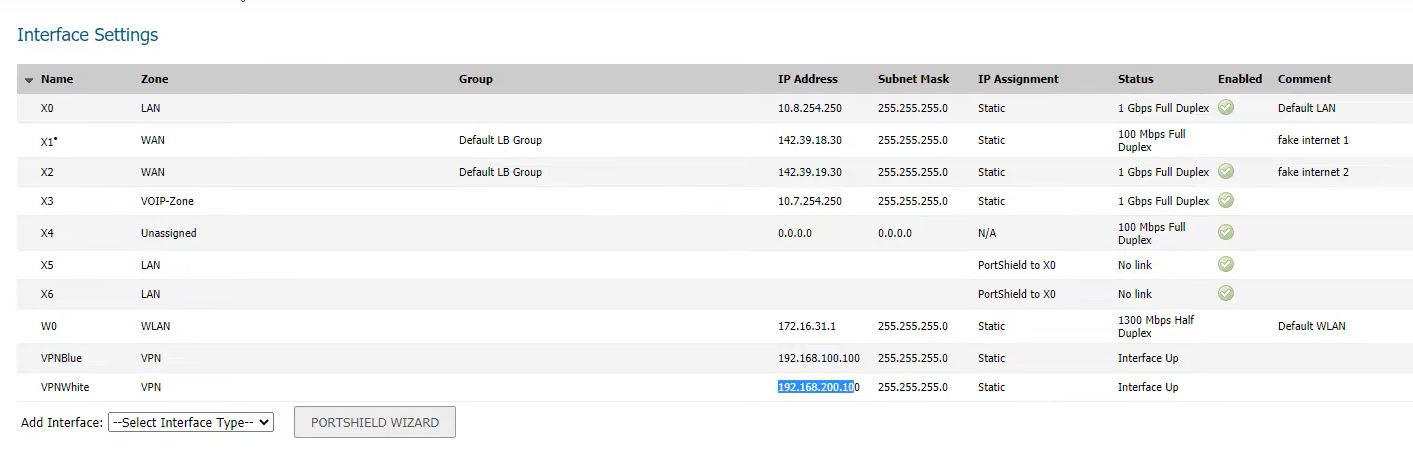
Overall interface in Main office firewall.
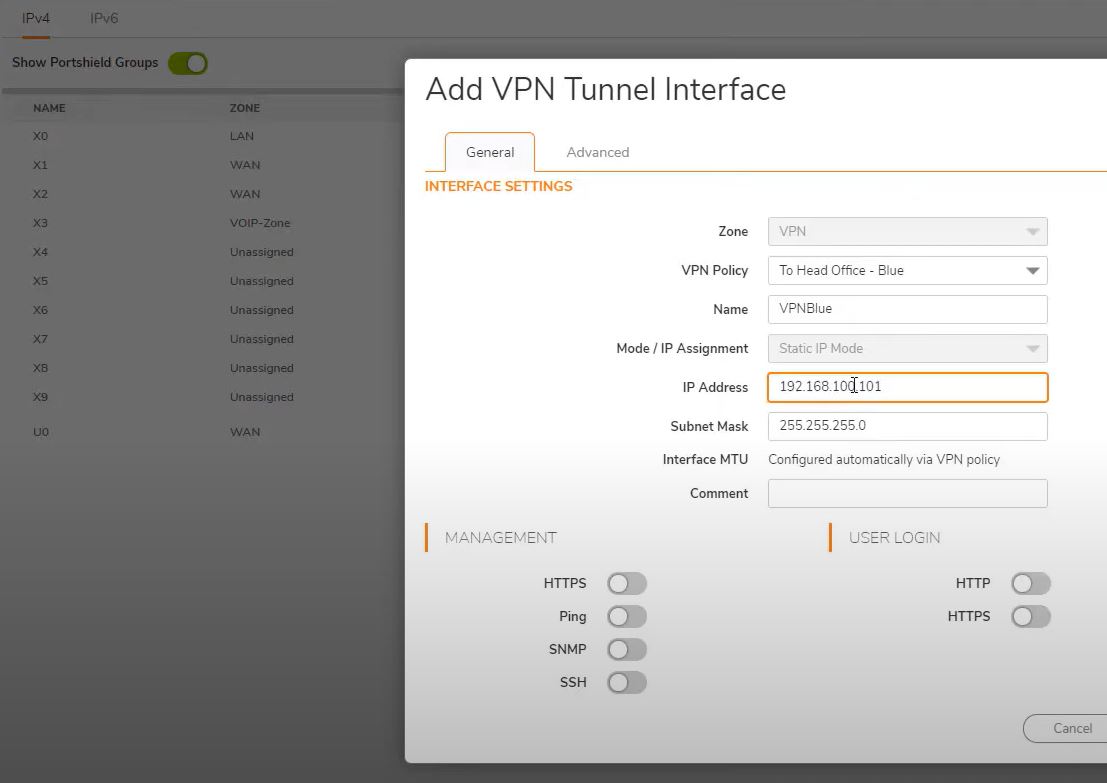
Remote office VPN interface creation- Blue
Go to Network->interface->Add interface->VPN Tunnel Interface
Zone:VPN
VPN Policy: To Headoffice- Blue
Name: VPNBlue
Mode: Static IP Mode
IP Address: 192.168.100.101
Subnet Mask: 255.255.255.0
Remaining settings no changes.
Save
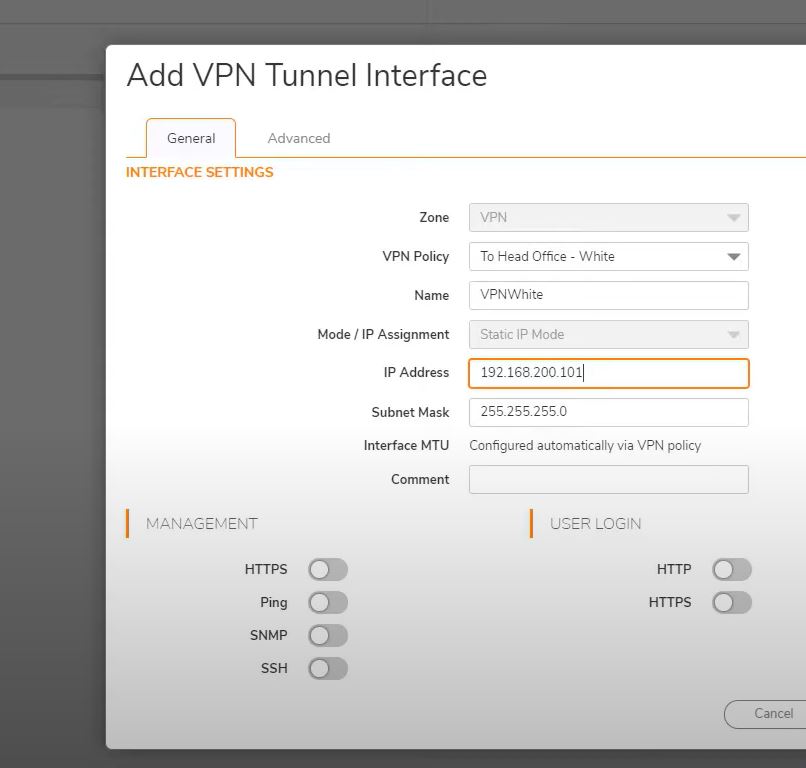
Remote office VPN interface creation- White
Go to Network->interface->Add interface->VPN Tunnel Interface
Zone:VPN
VPN Policy: To Headoffice- White
Name: VPNWhite
Mode: Static IP Mode
IP Address: 192.168.200.101
Subnet Mask: 255.255.255.0
Remaining settings no changes.
Save
Overall VPN interface in Remote firewall
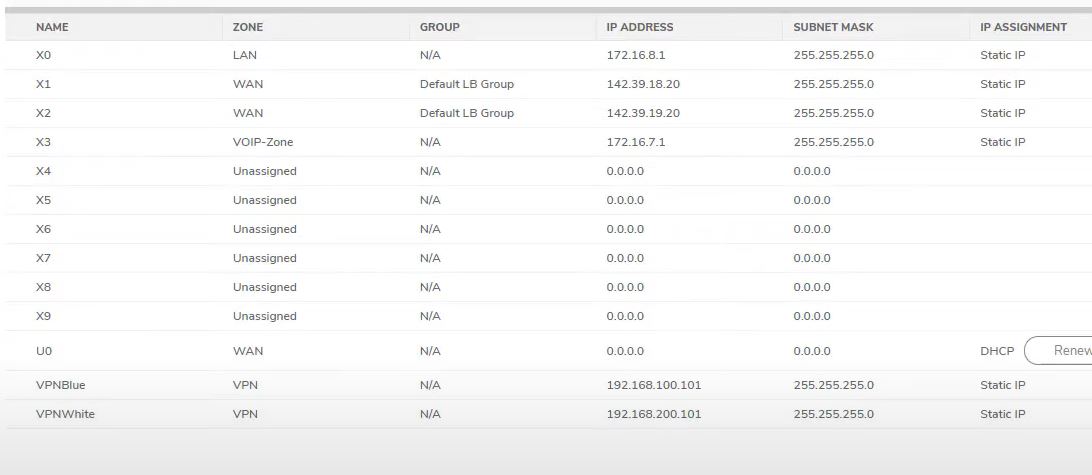
SD-WAN – Making routing for two VPN
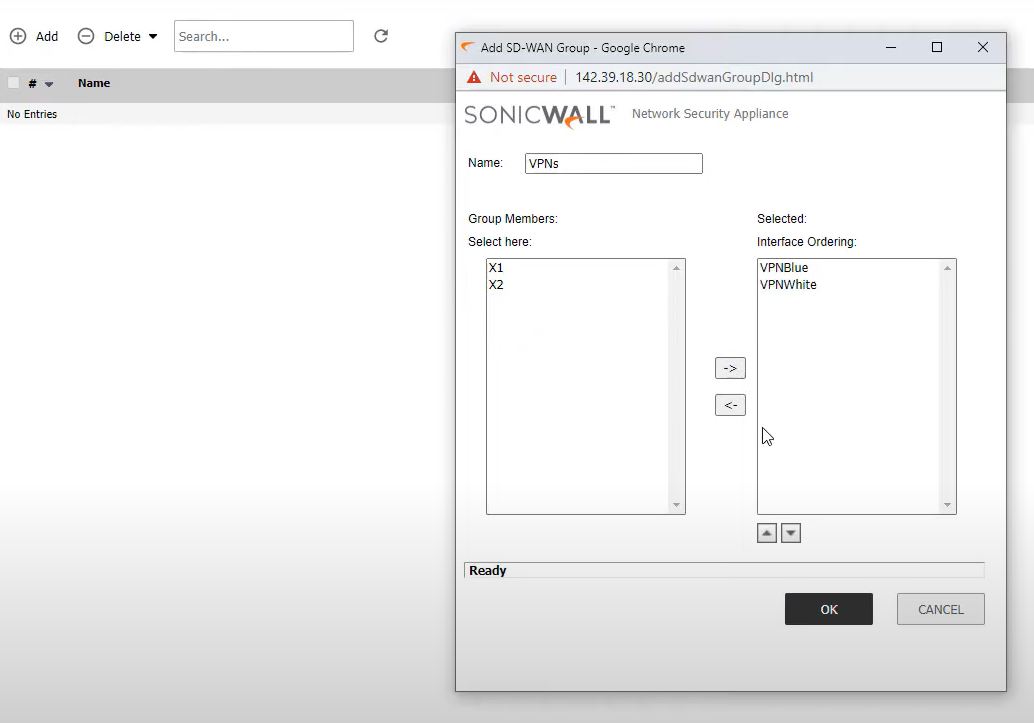
First Go to Remote firewall and create SDWAN Group then add both vpn interface.
Network->SDWAN->Groups
Name: VPNs
Add: VPNBlue
ADd: VPNWhite
Save
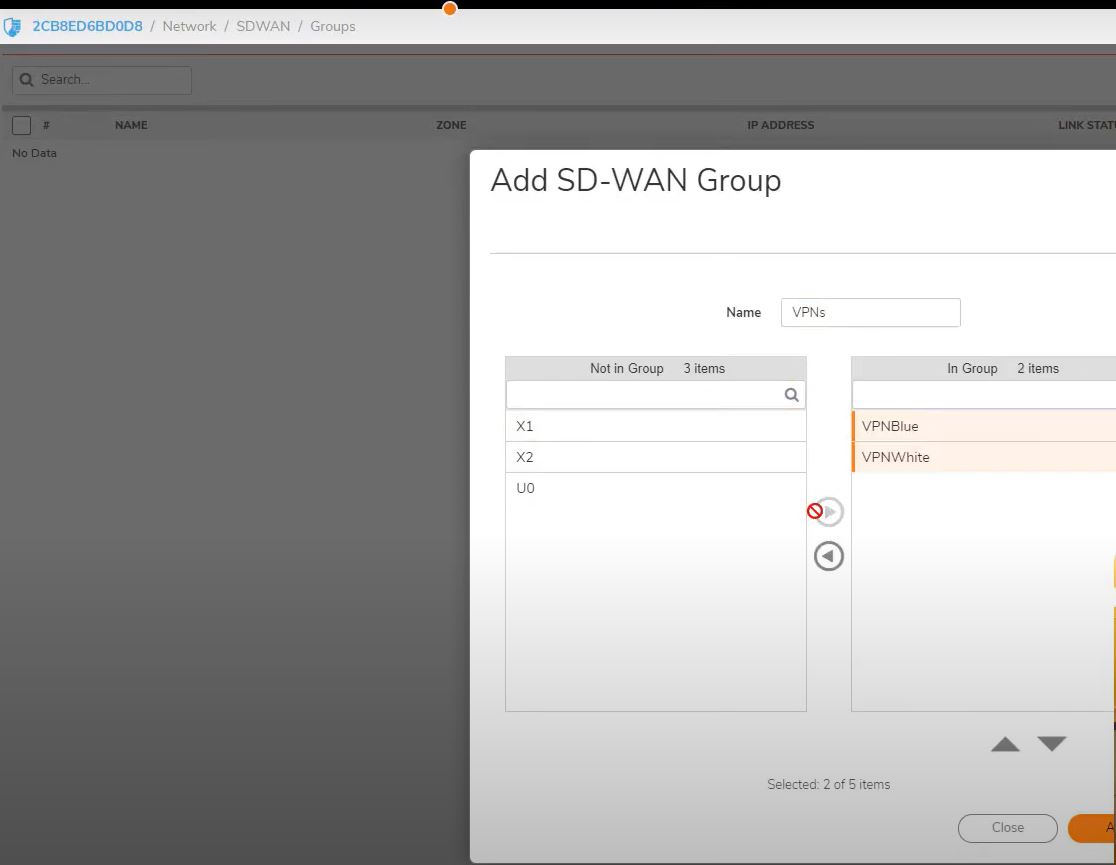
NeXT
SLA Class object
Generating maximum latency and jitter from network.
in the example VOIP connection have some latency and jitter.
SDWAN->SLA Class Object-> Add
Name: Voip
Include latency: ON
Latency (ms): 100
Include jitter: ON
Jitter (ms): 30
SAVE
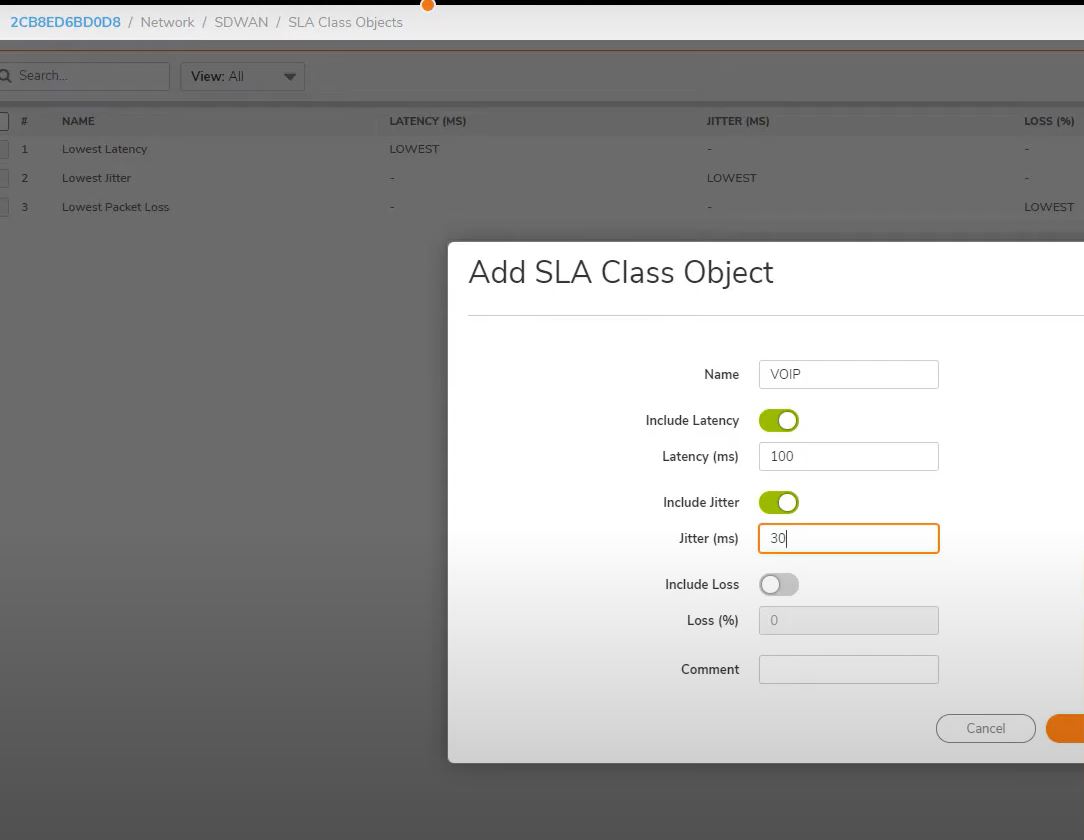
NEXT
Path selection Profiles
SDWAN->Path Selection Profiles->Add
Name: VOIP
SDWAN Group: VPNs
SLA Probe: VPN Probe -VPNs
SLA Class Object: VOIP
Backup Interface: VPNBlue
SAVE
Next
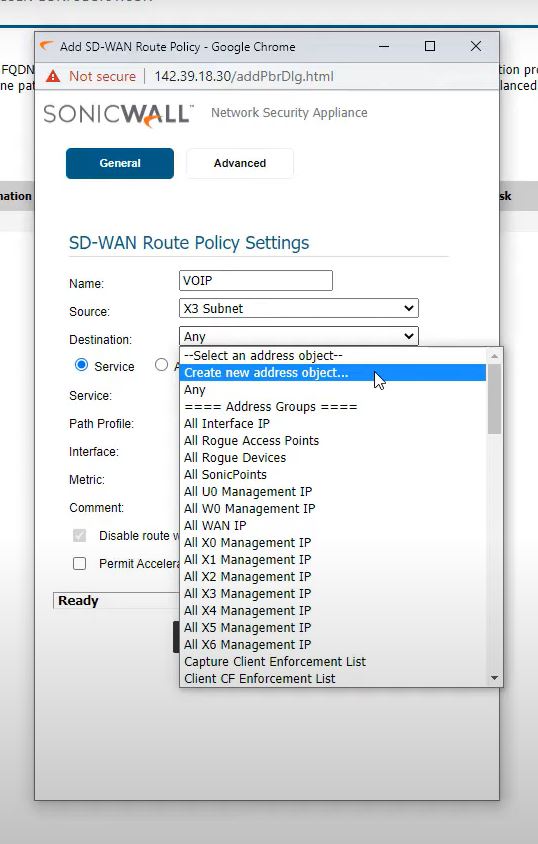
Rules
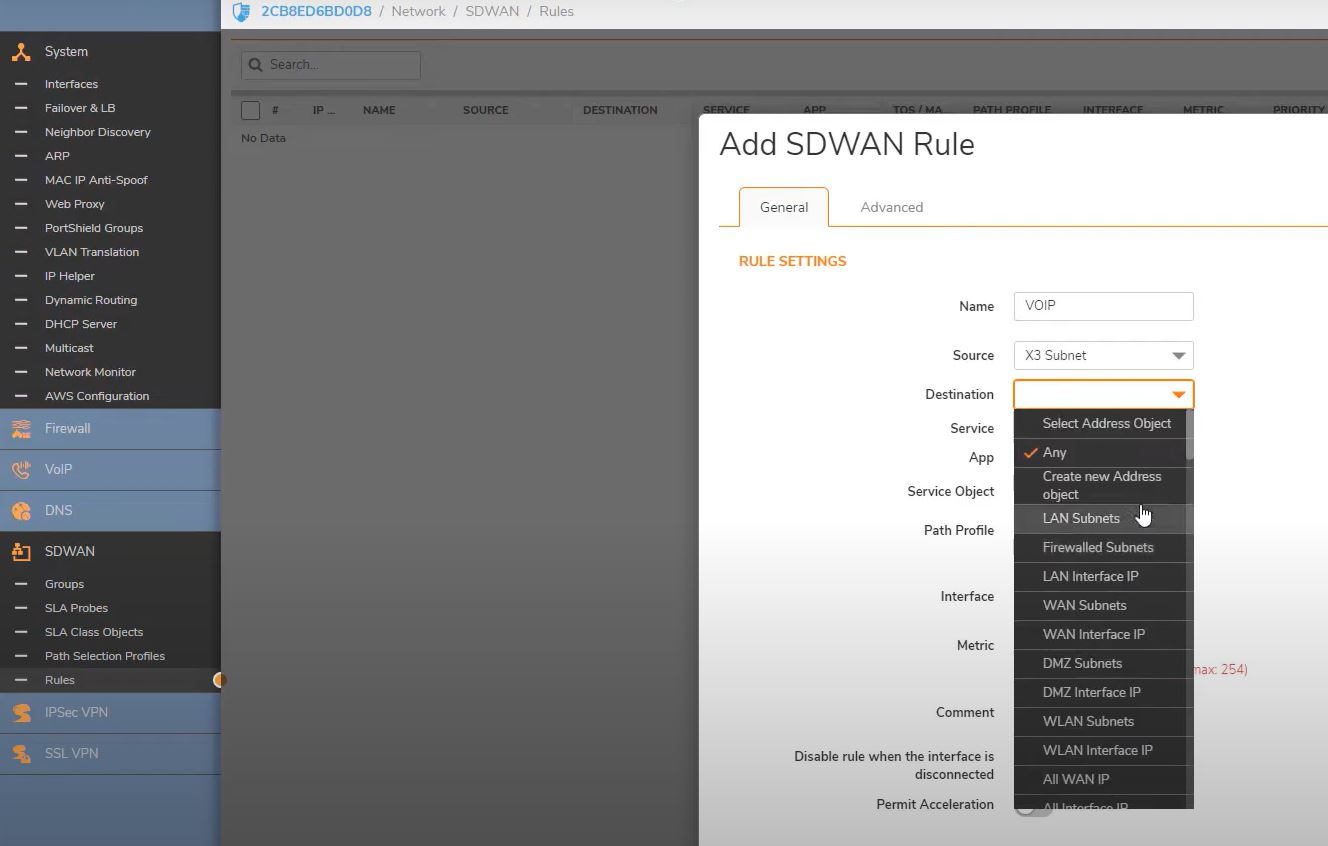
SDWAN->Rules->Add SDWAN Rules
Name: Voip
Source: X3 Subnet
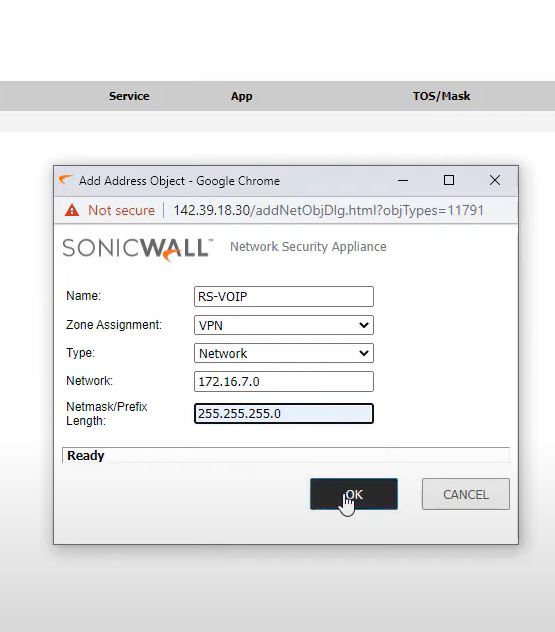
Destination: Not created then create Address object
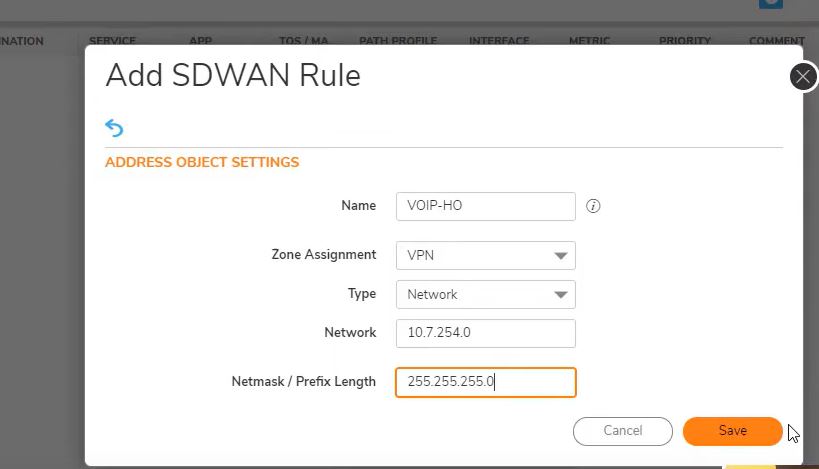
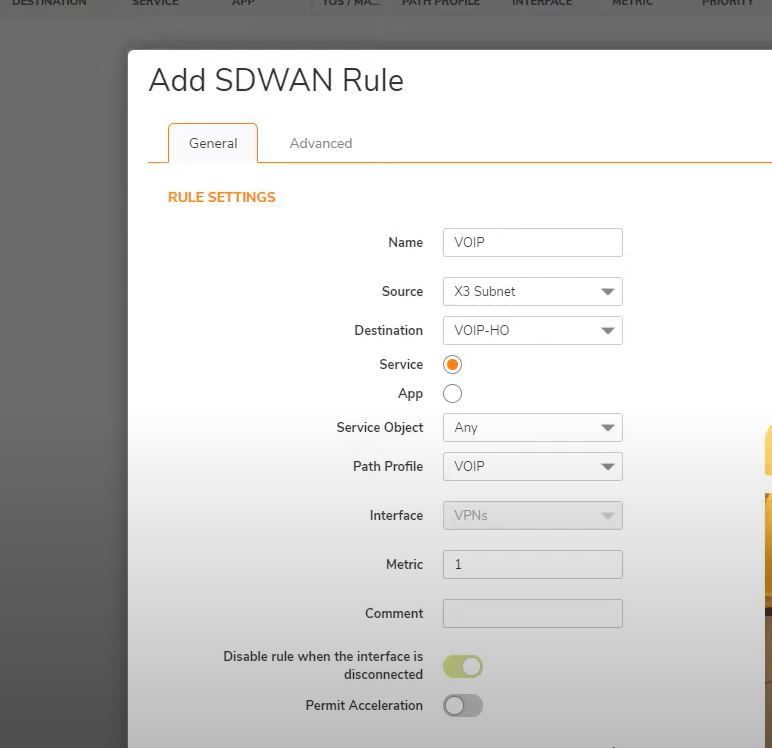
Now same step on main office firewall
Creating SD WAN Group on main office
SDWAN Groups
SDWAN->SD-WAN Groups- > Add
Both vpn on a group: VPNs
Performance class object
SDWAN->Performance class object->Add
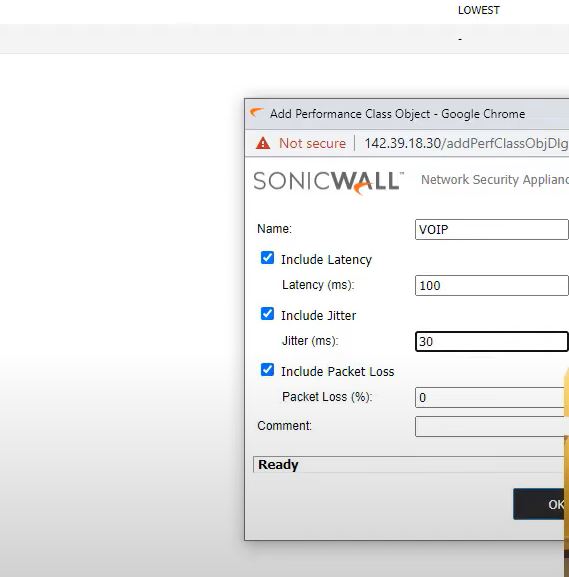
Path Selection Profiles
SDWAN->Path selection Profiles->Add
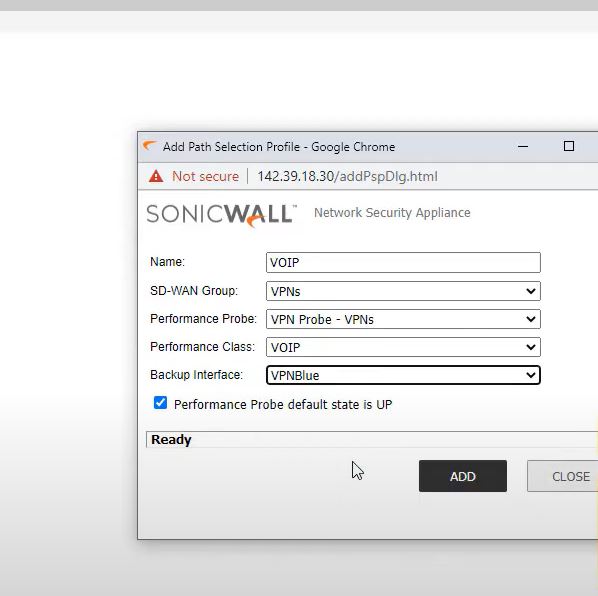
SD-WAN Route Policy
SDWAN->SDWAN Route Policies->Add
Create new address object
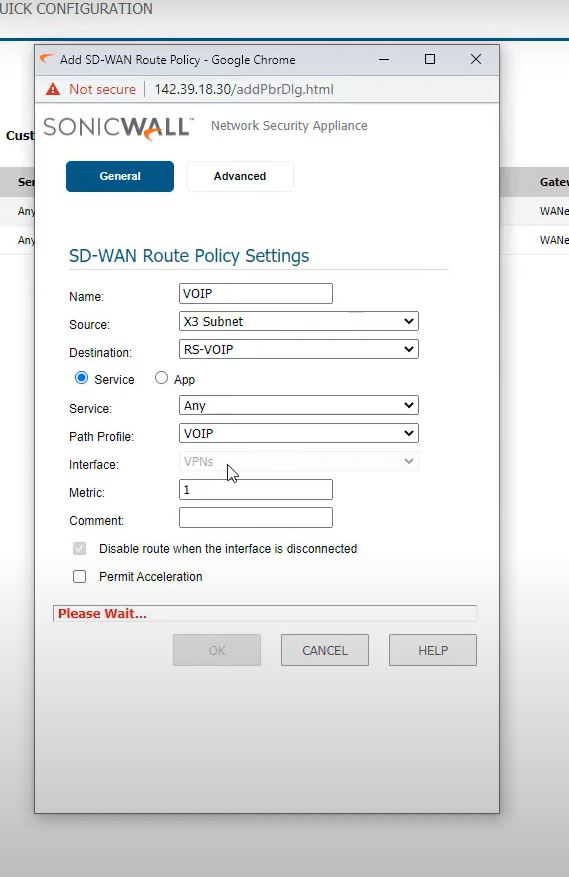
That’s all routing on Main office firewall SD WAN.
Now VPN connection VOIP up and running.